WFH: More than a Temporary Transition
A number of our clients have asked us how to leverage the NIST Cybersecurity Framework (NIST CSF) to address work-from-home cyber risk. Considering the global prevalence of remote work well into 2021, the concern deserves attention and can easily be addressed in the Axio360 platform. With these continued and dramatic changes in the work environment, it’s more important than ever to be prepared for a complex and expanded cyber-attack surface.
Cyber Risks Introduced by Remote & Hybrid Work Arrangements
As the pandemic surfaced last year, there was a hurried initiative by organizations to shift work operations from onsite to work from home. In an effort to maintain the continuity of business operations in the frenzy caused by COVID19, security took a backseat. There was no other choice as organizations were caught in an unprecedented situation. IT and security teams were pressed to deploy mechanisms that gave employees urgent remote access to the company’s systems and processes.
However, there’s no denying the fact that the shift in the working mode has introduced risks to an organization’s physical, personnel, and systems’ security.
As employees use their personal devices – which they use for varied other purposes outside of work such as entertainment, gaming, and shopping – for work and connect to personal internet networks to send confidential organizational and client data, the vulnerability of an organization to cyber attacks and thefts exponentially increases. And so does the potential for expensive lawsuits, fines, and penalties for breach of sensitive data.
The hybrid work arrangement, where some employees work from home and others work onsite, introduces further risks as on-premises workers connect and collaborate and exchange information and documents with remote workers who may be using rogue or outdated devices, vulnerable home networks, and/or weak passwords.
But that’s not all. Data accessed, processed, transferred, and uploaded to the cloud over poorly managed home networks and weak security protocols exposes an organization’s susceptibility to attacks. All in all, given the umpteen types of risks from disparate sources and the nature of the gigantic internet, there is no defined or finite parameter of the attacks to prepare against. The surface for attacks has expanded with no set boundaries. The question is: how to address such undefined remote work cybersecurity risk?
50 Considerations for Enhancing Security with NIST-CSF Assessments
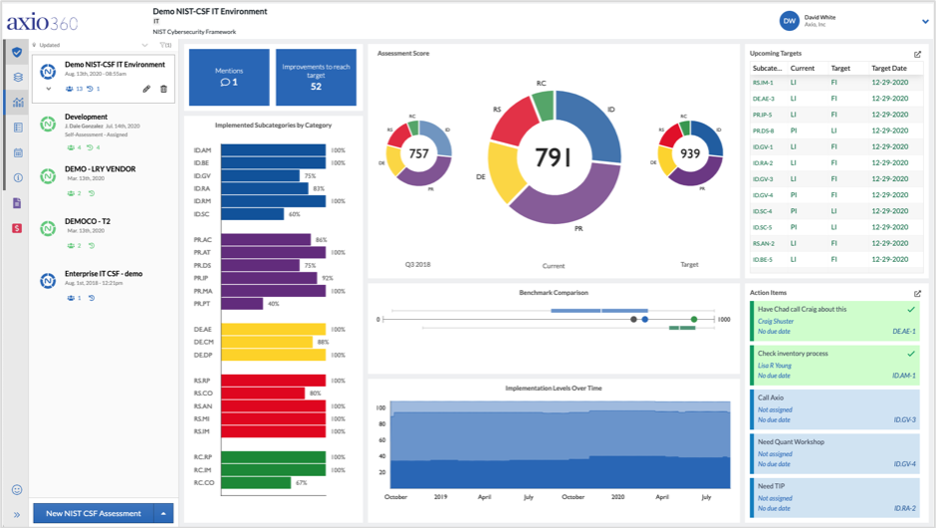
This blog post highlights 50 considerations for enhancing your remote work cybersecurity that are mapped to NIST CSF. Keep these considerations in mind as you complete your NIST CSF assessments in the Axio360 Platform. NIST CSF contains 5 Functions, 23 Categories, and 108 Subcategories; the considerations are organized by the NIST CSF Functions: Identify, Protect, Detect, Respond, and Recover and grouped by the 23 NIST CSF Categories.
Table of Contents
NIST CSF Tips by Function
ID: Identify
The first NIST CSF Function, Identify, drives home the importance of understanding what remote work cybersecurity risks the organization is susceptible to before going about putting protections in place. With more and more endpoints and with many of those now being on employee-provided networks, the risks of data leakage are becoming exponentially higher.
ID.AM: Asset Management
- Track assets that are moving off-prem (from previously situated on-prem) in inventories.
- Configure, vet, and track new assets that are acquired in response to remote work.
- Identify any newly allowed BYODs accessing network (via VDI, VPN, etc.).
- Revise processes to provision assets to remote employees.
- Track the changes to configuration baselines necessary for remote work.
- Create new configuration baselines for new devices acquired for remote work (and track the absence of those baselines for things like BYOD).
- Revise processes to configure newly provisioned assets.
ID.BE: Business Environment
- Adjust employee onboarding and off-boarding processes for social distance guidelines and travel restrictions.
ID.GV: Governance
- Monitor employee absenteeism to ensure that vital remote work cybersecurity processes are appropriately staffed.
- Review policies and add any needed deviations to provide for remote work during the emergency.
ID.RA: Risk Assessment
- Re-assess risks that have changed or will change as a result of remote work.
- Increase the cadence of risk reviews.
- Ensure that the organization is collecting new threat data related to threat actors and threat actor campaigns targeting remote workforce or exploiting the current situation.
ID.RM: Risk Management Strategy
- Integrate risk assessment and decisions in your COVID-19 response activities.
- Document any significant changes to the security strategy and program based on new remote work cybersecurity risks and obtain senior management authorization.
ID.SC: Supply Chain Risk Management
- Ensure that critical vendors can continue to support you per agreed SLAs and with remote service as appropriate.
- Review pandemic response plans and activities for key vendors.
- Increase monitoring on business conditions to identify critical suppliers that may be in financial distress.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cybersecurity Risk
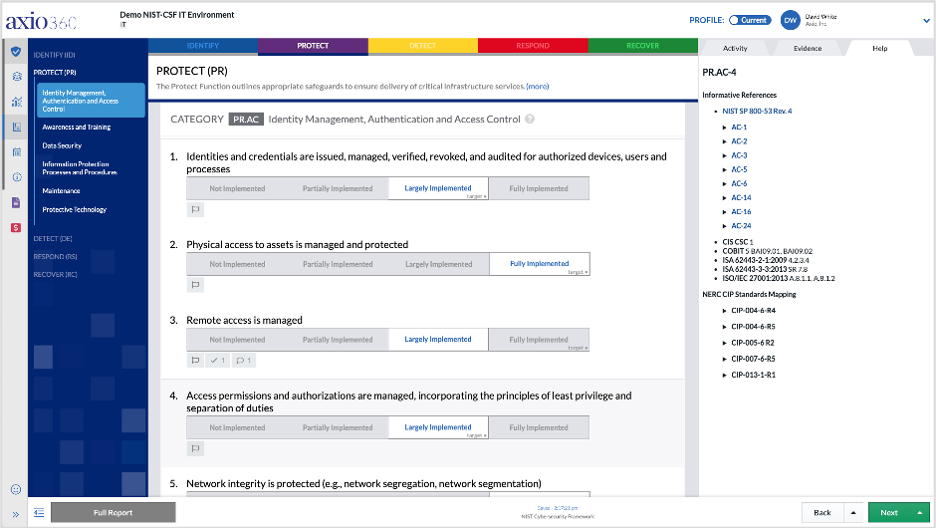
PR: Protect
Once the organization has a grasp of the systems, assets, data, and capabilities in its environment and their associated risks, the next Function, Protect, guides actions for deciding what specific steps to take to protect them.
During the pandemic and lockdown, users have had fewer options for “off-work” hours. This has resulted in an increased engagement across devices and more opportunities for exploitation.
PR.AC: Identity Management, Authentication and Access Control
- Make sure that all accounts that are used for remote access have been approved and documented.
- Ensure remote access requires strong (multifactor) authentication.
- Limit administrative/privileged accounts from remote locations. Instead, authenticate through non-privileged accounts and escalate to privileged accounts internally.
- Determine which functions should not be authorized for remote access (i.e., certain operations must be done on-prem).
- Document authorization adjustments (when increased access is needed) in order to reverse them when the crisis is over.
- Based on the number of people no longer working in the office, tighten physical access to the premises if needed.
PR.AT: Awareness and Training
- Roll out specific training for effective, safe, and secure remote work practices.
- Launch awareness campaigns for threats targeting remote work (e.g., credential scraping, phishing).
- Launch awareness campaigns for threats leveraging the COVID-19 crisis.
- Launch training and awareness on secure remote work issues (e.g., who can use company assets).
PR.DS: Data Security
- Evaluate data that is moving to unsecured environments or networks (e.g., home networks), and data that can now be accessed from those unsecured environments.
PR.IP: Information Protection Processes and Procedures
- Review and adjust security controls and configurations on assets that are moving onto untrusted networks (e.g., home networks) given absence of network security controls.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cybersecurity Risk
DE: Detect
The third NIST CSF Function focuses on the need to be able to effectively Detect when a cybersecurity event may be occurring and know what to look for. The FBI has reported a 400% increase in cyber incidents since March 2020.
DE.AE: Anomalies and Events
- Adjust baseline thresholds to reflect the increase in remote work (i.e., what is acceptable, “normal” behavior and access).
- Detect behavior that exceeds those new baseline thresholds.
DE.CM: Security Continuous Monitoring
- Monitor for approved account access, explicitly noting access from non-approved accounts.
- Determine mechanisms to address vulnerabilities (i.e., scanning, patching) on remote assets.
- Incorporate newly acquired classes of assets in vulnerability processes.
DE.DP: Detection Processes
- Ensure logging provides visibility on endpoints that are remote, the remote connections, and associated activity.
- Ensure that monitoring capabilities can be accessed remotely if necessary.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cybersecurity Risk
RS: Respond
The fourth NIST CSF Function is based on the fact that no organization is immune from a cybersecurity event, no matter how proactive it has been; so it is important to prepare to Respond to remote work cybersecurity events.
In the times of COVID 19, ransomware’s latest tactic is a conversion to doxware. The attacker infiltrates your data and threatens to notify your customers that you have been hacked and that sensitive customer data is being held. So even if you have backups and don’t pay the hackers, your reputation is still at risk. How do you respond properly?
RS.RP: Response Planning
- Review and adjust thresholds based on new remote work cybersecurity risks for incident declaration.
- Adjust response team membership to provide additional backup team members.
- Evaluate your ability to respond remotely to incidents and adjust plans and technology accordingly.
- Ensure that third-party response resources (e.g., outsourced forensics) remain available and can support you remotely.
RS.CO: Communications
- Alert the workforce of specific remote work cybersecurity threats due to COVID-19 or other campaigns currently targeting your organization.
RS.MI: Mitigation
- Ensure bandwidth availability for remote patching protocols over allowed access paths.
- Implement the ability to exclude (or quarantine) assets that don’t meet configuration/security baselines.
- Implement the ability to sever connections with remote endpoints that are compromised, without depending endpoint functionality.
RS.IM: Improvements
- Update response plans based on lessons learned that can come from responding to events with a remote workforce.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cybersecurity Risk
RC: Recover
Finally, the fifth NIST CSF Function, Recover, helps organizations get back to normal after a cyber event. With a more remote workforce, additional considerations may be necessary.
RC.RP: Recovery Planning
- Determine if the DR/BC plans are sufficient or need revision in light of the current pandemic response.
- Begin planning the “return to normal” strategy.
RC.IM: Improvements
- Revise current business continuity and pandemic response plans with any new lessons learned during this crisis and especially any identified remote work cybersecurity threats.
- Review resources necessary to support the changing program during an emergency, such as a pandemic.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cybersecurity Risk
Getting Started with NIST CSF for Your Remote Workforce
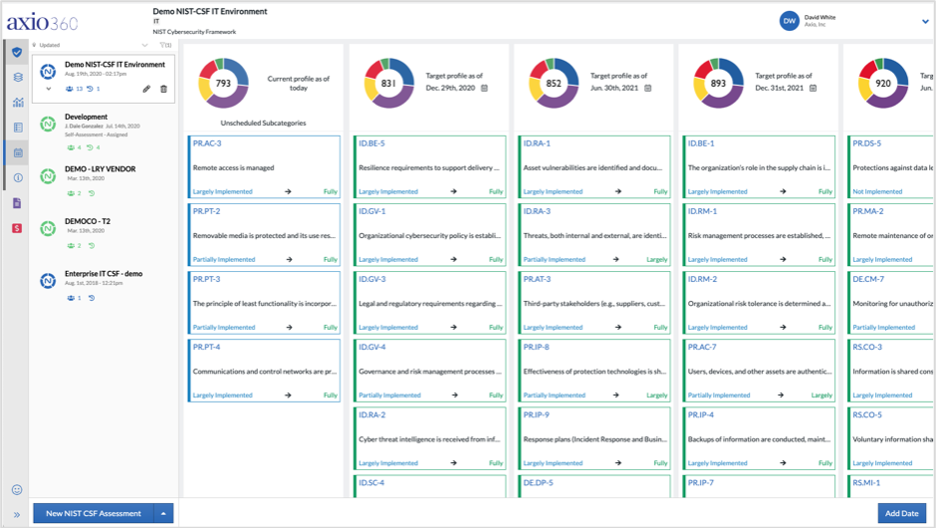
The Axio360 platform is the easiest and fastest way to get started with NIST CSF. With the considerations above, you are well on your way to optimizing your work-from-home or remote work cybersecurity program. If you’d like to learn more information and dive into more detail on how to perform a NIST CSF assessment in Axio360, you can book a demo and speak with one of our experts.
Download this handy checklist as you go through your NIST CSF assessment.
Axio’s Top 50 NIST CSF Tips to Address Remote Work Cyber Risk
About the author: Craig Shuster is Axio’s VP of Cyber Risk Engineering




