Some of the common questions we encounter while building cybersecurity programs for organizations include: What is the NIST cybersecurity framework exactly? What do the functions of the NIST CSF help us achieve? How does one develop the NIST cybersecurity framework roadmap?
For those of you who want to learn more about the framework, we here at Axio Global provide a guide to understanding the NIST CSF functions and answers some commonly asked questions pertaining to the cyber risk management framework. Understanding what the NIST CSF functions are, and why they are important is a critical step in getting started with the framework.
The NIST Cybersecurity Framework (CSF) is voluntary guidance aiming to help organizations better manage and reduce cybersecurity risk. It is based on existing standards, guidelines, and practices that have proven to be effective in improving the cybersecurity strength. Implementing the NIST CSF is a great way to introduce structure into an organization’s cybersecurity program and enhance their ability to effectively tackle cyber events with minimum damage and prevent their occurrence in the future.
Since it facilitates proper planning and execution of your cyber security program, it’s safe to say that the NIST CSF is essentially an implementation planning tool. It can be used to help identify and prioritize actions for reducing cybersecurity risk, and it is a tool for aligning policy, business, and technological approaches to managing that risk.
The framework has a core set of cybersecurity activities organized at three levels:
- Functions
- Categories
- Subcategories
- Categories
The Important Distinction of Functions in the NIST CSF
The three activities we have structured above are very unique and serve very specific purposes for taking charge of an organization’s cybersecurity posture. Sometimes these activities are used interchangeably in conversation, particularly by someone who has not had a chance to take a deeper dive into how the framework is organized.
In this post we aim to explain the important distinction of the functions in the NIST CSF implementation planning tool and show how they can be utilized in an efficient and dynamic way for planning your cybersecurity program.
NIST CSF Functions organize basic cybersecurity activities at their highest level. These Functions are:
- Identify
- Protect
- Detect
- Respond
- Recover
Functions are meant to intuitively organize aspects of cybersecurity to support decision making, risk management, addressing of threats, and continual improvement based on lessons learned. Functions include the activities to take prior to a cybersecurity event (Identify, Protect, Detect) as well as what to do after one occurs (Respond and Recover).
How NIST CSF Functions are Structured in the Framework
Before implementing the NIST CSF, it’s important to understand the organization of the functions in the framework. First and foremost, each NIST CSF function is subdivided into a number of categories, each of which describes a group of outcomes that are recommended as part of the function. Each category is further subdivided into subcategories. Each subcategory defines a specific recommended outcome. Informative references are the existing standards, guidelines, and practices that are mapped to each subcategory. So, in essence, they help us understand each subcategory better.
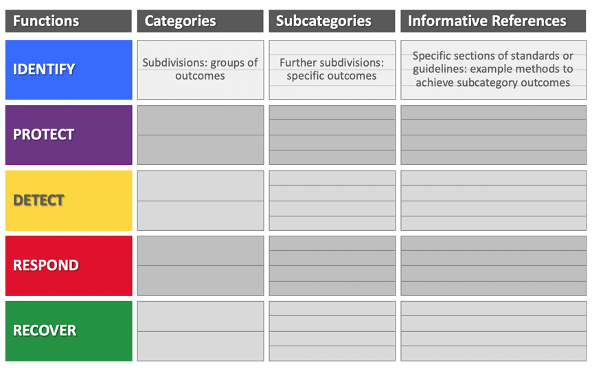
NIST CSF contains 5 Functions, 23 Categories, and 108 Subcategories
NIST CSF Functions Communicate Cyber Risk Clearly to all Stakeholders
Owing to the logical progression they describe, the NIST CSF functions can be leveraged when communicating cybersecurity risk to both technical and non-technical audiences such as senior leadership and Boards of Directors.
The NIST CSF can be credited with facilitating the increase of both the awareness and significance of cybersecurity risk. In fact one of its great successes is that the world now commonly speaks of cybersecurity in terms of Identify, Protect, Detect, Respond, and Recover.
A Closer Look at the 5 Functions of NIST CSF
In order to design and put into practice a comprehensive cybersecurity program that is both robust and effective, the first step is to develop a NIST Cybersecurity framework roadmap. It must ideally include a plan to incorporate all five functions that form its core. Here we examine each of the primary functions in the NIST CSF implementation planning tool.
1. Identify
Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
The first function, Identify, drives home the importance of understanding what cybersecurity risks the organization is susceptible to before going about putting protections in place.
Example outcomes for the Identify function include:
- Identifying physical and software assets to establish an asset management program
- Establishing cybersecurity roles, responsibilities, and policies to define a governance program
- Defining a risk management strategy and risk assessment processes for the organization
2. Protect
Develop and implement appropriate safeguards to ensure delivery of critical services.
Once the organization has a grasp of the systems, assets, data, and capabilities in its environment and their associated risks, the next function, Protect, guides actions for deciding what specific steps to take to protect them.
Example outcomes for the Protect function include:
- Implementing controls to protect the confidentiality, integrity, and availability of data
- Managing protective technologies to ensure the security and resilience of systems and assets
- Empowering and enabling staff through awareness and training activities
3. Detect
Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
The third activity is detect – organizations need to be able to effectively detect when a cybersecurity event may be occurring and to this end, they must know what to look for.
Example outcomes for the Detect function include:
- Implementing continuous monitoring to identify cybersecurity events and verify protections
- Ensuring that anomalies and events are detected, and their potential impact is understood
- Testing and maintaining detection processes to ensure awareness of anomalous events
4. Respond
Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
Fourth, no organization is immune from cybersecurity events no matter how proactive it has been, so it is important to prepare for the steps needed after a cybersecurity event takes place.
Example outcomes for the Respond function include:
- Ensuring response plans are executed during or after an incident
- Coordinating and managing communications inside and outside the organization during a response
- Analyzing effectiveness of response activities
5. Recover
Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
The last function is Recover – organizations have to get back to normal operations after a cyber security event.
Example outcomes for the Recover function include:
- Ensuring the organization implements recovery planning processes and procedures
- Implementing improvements based on lessons learned
- Coordinating communications during recovery activities
We recently worked with a hospital CISO to implement NIST CSF using the Axio360 platform
Earlier in the article we talked about how the NIST CSF functions can be leveraged when communicating cybersecurity risk to both technical and non-technical audiences such as senior leadership and Boards of Directors. Senior cybersecurity leaders need to be thoughtful in their approach standardize and modernize risk and security controls while reporting progress to the Board.
 A CISO of a well-known hospital system recently approached Axio to help his organization standardize enterprise cybersecurity at its own pace without increased complexity or framework limitations.
A CISO of a well-known hospital system recently approached Axio to help his organization standardize enterprise cybersecurity at its own pace without increased complexity or framework limitations.
Hospitals, insurers, and providers of medical services are increasingly vulnerable to malicious cybercriminal activity. Private health records maybe breached, patient care disrupted through ransomware attacks, and IoT monitoring data manipulated to create chaos and confusion
The CISO had looked at a lot of solutions but none of them were robust enough to manage the organization’s cyber risk posture.
Some pain points the hospital CISO expressed to us included:
- Frameworks such as HI Trust were time-consuming, and limited in their flexibility to easily report progress across various security domains
- They were looking for a collaborative platform to get out of spreadsheets to standardize risk and security controls, as well as report progress to executive stakeholders
- Beyond a platform subscription, they also wanted a long-term partner with extensive knowledge in the healthcare industry and evolving threat landscape.
As both a payer and provider of health services, the hospital system’s information security team needed to build a cybersecurity standard for the entire organization. Legislative changes such as HR 7898 have incentivized healthcare orgs to adopt cybersecurity frameworks such as NIST CSF, resulting reduced audit cycles and abated fines.
Axio360 offered the hospital system foundational reporting with the ability to map and scale to more comprehensive frameworks and maturity models in the future.
Axio360 Solution benefits include:
- Rapid onboarding to accelerate collaboration and transition away from spreadsheets
- Easy documentation capabilities for centralized point-of truth evidence collection
- Flexible PDF reporting, custom views for various executives and board members
- A long-term trusted relationship with Axio’s healthcare professional services team.
You can learn more about how NIST CSF helps hospitals and healthcare systems in the face of growing cyber attacks by exploring our article on the topic.
NIST CSF Implementation Planning Tool in the Axio360 Platform
The 5 Functions serve as the broadest starting point in completing an assessment of your cybersecurity program’s NIST CSF maturity levels. The Axio360 platform integrates the NIST CSF into its Cyber Program Assessment, Planning, and Management functionality.
Through Axio360 the NIST CSF implementation planning tool can be used to:
- Manage and improve the health of your cyber program, with company-wide transparency.
- Benchmark your cybersecurity program to see how well it stacks up to its peers.
- Create and manage a target profile and workplan for improvement.
- Continually share progress with company leadership and the Board with dynamic dashboards and generated reports.
Complete your NIST CSF assessment for free today.
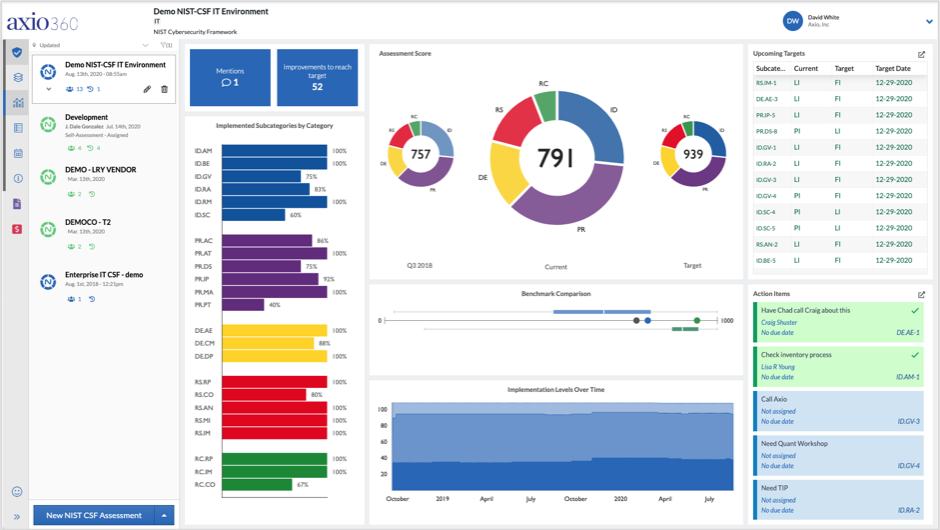 Axio360 NIST CSF Assessment Dashboard
Axio360 NIST CSF Assessment Dashboard
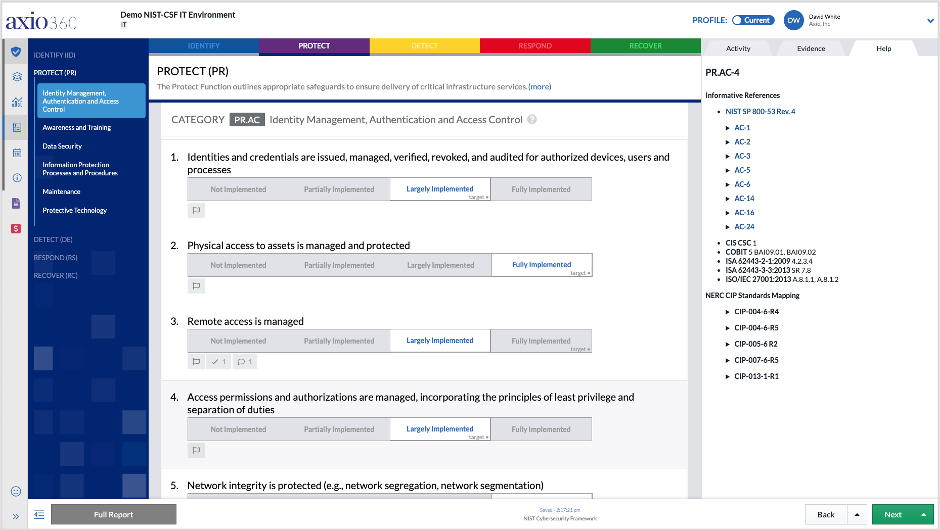 Axio360 NIST CSF Assessment and Target Profile Interface
Axio360 NIST CSF Assessment and Target Profile Interface
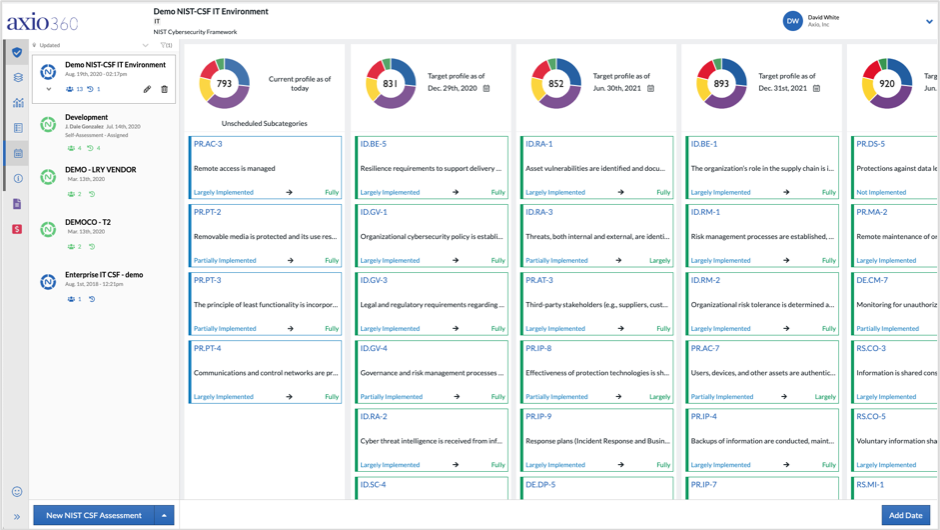 Axio360 NIST CSF Roadmap Planning Tool
Axio360 NIST CSF Roadmap Planning Tool
If you’d like to experience the complete functionality of the NIST CSF implementation planning tool and discuss your particular use case for the framework, our experts are standing by.
Get started by booking a demo.
About the author: Wassie Goushe is a senior cybersecurity engineer at Axio.




