In protecting an organization from cyber risk, clarity about the effectiveness of its cybersecurity program is imperative. The organization must understand its security posture and identify gaps in safeguards to ensure that security investments align with the organization’s risk appetite. Performing assessments using a reference framework, such as the NIST Cybersecurity Framework (CSF), provides the means for evaluating current cybersecurity posture and potentially identifying risk for further analysis. Additionally, the use of NIST CSF to create a current profile (where the organization stands at the time of the assessment relative to each control) and a target profile (where the organization would like to be at some future date relative to each control) helps in identifying gaps in a cybersecurity program and establishing areas for improvement in a consistent and methodical manner.
Getting started: Defining the scope
While the NIST CSF was designed for critical infrastructure, it is inherently flexible, which means assessments using it can be tailored in an appropriate manner regardless of company size or industry. Prior to the start of any assessment, the critical first step is to identify the scope, or what part of the organization is going to be assessed. Due to the flexible nature of CSF, assessments can be scoped to an entire enterprise, a major network (e.g., business network or OT network), a subset of the organization such as a specific business unit, or even a single IT or OT system.
When determining the scope of a CSF assessment, organizations should also bear in mind potential downstream functions and systems. The graphic below illustrates how these considerations can come into play. Let’s assume an organization wants to perform an assessment on an organizational unit (1.3). The downstream flows of that unit (1.3.2, 1.3.2.1, etc.) could represent critical processes, systems, asset classes, or a combination thereof. If the assessment scope includes all of the organizational unit, then these subordinate levels are also in scope.
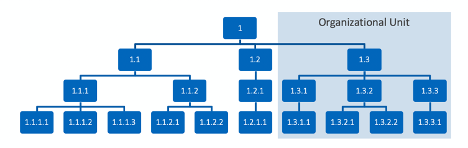
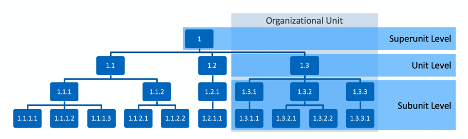
In many circumstances, a single assessment on an organizational unit is not appropriate because cybersecurity is not consistently managed across the unit. In instances where this is the case, multiple assessments may be required, examining practices at the superunit, unit, and subunit levels separately. Understanding the scope and quantity of assessments prior to starting will allow the organization to create efficiencies, inform the appropriate stakeholders, and determine what information is required to achieve organizational goals.
Still unsure where to begin?
At times, scoping an assessment is easier said than done. These are some key considerations that may assist in scoping assessments:
- Does the unit organize and manage by process, by asset, or some combination?
- What are the key processes or asset categories for the unit?
- How does the cybersecurity program vary by asset class or critical process?
- Does the unit outsource certain cybersecurity functions to another unit?
If you are still unsure where to begin, it is best practice to select a part (or parts) of the organization where cybersecurity is consistently managed. It may also be beneficial to answer the questions in the following scoping exercise:
- What is the minimum number of assessments needed to characterize the business unit?
- For each of those assessments, what is the organizational scope?
- Who are the key stakeholders that will need to be involved?
- Are there previous assessments that can be leveraged as a starting point?
- What is the desired sequence or prioritization for the assessments?
What’s next?
Assessing your organization shouldn’t be a daunting task. Once a scope has been determined, it is time to corral the proper stakeholders to complete the assessment(s). Keep in mind that in many cases a single enterprise assessment will not be sufficient and multiple tailored assessments will be required. Managing multiple assessments and providing meaningful output can be difficult, but it doesn’t have to be.
Axio360 assists organizations with managing and improving cybersecurity programs through the facilitation of continuous assessments (including NIST CSF), benchmarking, and improvement planning and tracking. Reporting and dashboarding within the platform makes communication with leadership approachable and consistent. For more information on how Axio can assist you with your NIST CSF assessments, please contact us.
About the author: Kelly Felder is a Senior Engineer of Cyber Risk Engineering at Axio



