Cyber Risk Assessments, Your Guide to a Secure Enterprise
With cyber threats prevalent in almost every industry, cyber risk assessments are an essential part of securing your organization. An assessment allows you to identify and understand which assets in your organization can be affected by cyber incidents. It measures what processes and controls you currently have in place to defend against potential cyber events. Similarly, NIST defines cyber risk assessment as “The process of identifying risks to agency operations (including mission, functions, image, or reputation), agency assets, or individuals by determining the probability of occurrence, the resulting impact, and additional security controls that would mitigate this impact.”
But why do I need a cyber risk assessment?
Cyber risk assessments allow you to thoroughly consider what type of risks you are exposed to. It’s hard to gauge the effectiveness of your program without conducting a security risk assessment. Assessments allow you to identify weak points in your program and address them. As the threat landscape changes and as organizations change, new cyber threats will arise. Continuous cyber risk assessment will allow leaders to identify these new potential threats and evaluate whether or not current controls are sufficient in protecting against them. Additionally, this cycle of continuous improvement allows for organizations to become more cyber resilient and grow their cyber maturity.
 On the other hand, certain industries mandate that organizations show compliance and hence they must conduct cyber risk assessments to do so. For example, those in the energy sector are subject to the NERC CIP requirements. Critical infrastructure is at the hands of these organizations and governments want to ensure that they are meeting these cybersecurity standards. Organizations can improve their cybersecurity program by using other frameworks to assess their current state while also checking that they are meeting these mandates.
On the other hand, certain industries mandate that organizations show compliance and hence they must conduct cyber risk assessments to do so. For example, those in the energy sector are subject to the NERC CIP requirements. Critical infrastructure is at the hands of these organizations and governments want to ensure that they are meeting these cybersecurity standards. Organizations can improve their cybersecurity program by using other frameworks to assess their current state while also checking that they are meeting these mandates.
So how do you begin an assessment?
- Finding the right people
- To begin a cyber risk assessment, it’s important to gather the right people in a room. Cybersecurity is no longer just an IT issue, it’s an enterprise issue. It will be useful to get experts from various functions of the organization into one room. These individuals should have extensive knowledge of their department, including the potential threats they may be facing and how they utilize technology.
- Select a suitable framework
- Next is to select a framework that will help you accomplish regulatory obligations while aligning with your company goals. These frameworks help you assess different functions with your organization, take inventory of controls while identifying vulnerabilities. There are many different types of frameworks. Based on your cyber program maturity and company goals and requirements, you can select a framework that works best for your organization.
- Utilize framework to determine weaknesses and deficiencies
- Frameworks will help you evaluate your cyber risk program. This includes identifying which controls you have in place and where you’re vulnerable.
- Lastly, use the score of your first security assessment to establish a baseline from which your cyber risk program can grow.
Types of Cyber Risk Assessment Frameworks
NIST CSF
The NIST Cybersecurity Framework (CSF) is a widespread framework that gained recognition for its fairness and objectivity. Use this framework to improve your cybersecurity risk management and identify gaps in your system. NIST CSF is organized at three levels: functions, categories and subcategories. You can easily integrate this framework with other industry standards such as NIST SP 800-53 and ISO 27001 and more.
C2M2
With 312 practices, 10 domains and 3 maturity levels, the Cybersecurity Capability Maturity Model (C2M2) is a thorough, comprehensive cybersecurity risk assessment. This model contains 3 maturity levels and within each maturity level are domains and their relevant objectives. To advance to the next maturity level, an organization must implement all practices within the previous level. C2M2 not only helps organizations identify what practices they currently have in place but also how they carry those practices out. This two-pronged approach of “what?” and “how?” allows users to thoroughly assess their cybersecurity program. Axio’s leaders have been closely involved in the development of C2M2.
CMMC
The Cybersecurity Maturity Model Certification consists of 5 levels of certification. Each of these levels reflect the maturity of a cybersecurity program and its resilience towards potential cyber events. Department of Defense contractors use these standards to secure their data and are assigned a maturity based on their cyber program. As organizations gain cyber resilience, they move onto the next level.
CIS20
The Center for Internet Security established 20 critical security controls that outline best practices for internet security. These best practices can help organizations shift from a compliance-based approach to a proactive cybersecurity approach. The CIS20 has 3 different sections – basic, foundational and organizational. Utilizing the CIS20 can improve your cybersecurity posture.
NERC CIP
The North American Electric Reliability Corporation Critical Infrastructure Protection standards are one of the few mandatory standards. These standards communicate security requirements to operate North America’s bulk electric system. Compliance is mandatory to protect the power grid. If an attack on critical infrastructure is successful, there can be a significant impact on the physical and economic well-being of society.
Please note that this list is not exhaustive of all cybersecurity frameworks and standards. With research and discussion, your organization can select a framework that is most suitable for your cyber risk assessment.
I’ve completed the assessment, now what?
Taking a cyber risk assessment is the first step, not the only step. Many organizations fail to take action after assessments and never use the results to improve their cybersecurity. Here is a list of steps to take after completing your assessment:
- Benchmarking – Organizations can benchmark their scores with peers to see how they stack up. These scores can give insight to whether more needs to be done to catch up with your peers or if the processes you have in place are enough.
- Road-mapping – Having actionable next steps after completing an assessment will allow you to roadmap towards improvement. This includes setting goals and targets within a reasonable time frame. Roadmaps are often adjusted, and deadlines are changed as your business changes and priorities shift.
- Re-assessing – After some time or after a few implementations, it’s useful to re-assess your organization to see the progress you’ve made. This can not only show leadership ROI but also help you decide what other controls or cyber insurance is needed to protect your organization.
Cyber Risk Assessments Made Effective with Axio360
The next steps after an assessment are often overlooked because organizations don’t have the time or resources. Some organizations may only take once-a-year assessments to appease auditors. However, neither of these approaches are enough to secure your organization. Cyber risk assessments can be a useful tool that helps you build resilience. At Axio we know that you and your team don’t have unlimited time or resources. That’s why our platform is both easy to use and comprehensive.
You can easily start an assessment of your company’s cyber risk by using Axio360. Our platform includes a variety of frameworks including NIST CSF, C2M2 and more. We can also work with your company to implement frameworks that you need. Additionally, Axio360 comes loaded with a variety of features that helps managing your cyber risk program more efficient.
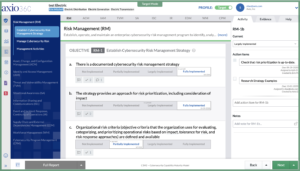
Within an assessment, you can create action items, assign them to team members and set deadlines. There’s also a space to include notes to jot down ideas, thoughts and comments. Each question in an assessment comes with a help text to give guidance while completing it. Users also have the capability to create a target profile to establish their cyber risk program goals. Moreover, users can easily share assessments and target profiles to empower collaboration.
To encourage continuous improvement, users can use our milestone feature to documents scores at a certain time to show progress. To roadmap towards your target, use our Kanban board to create and adjust your plans. This feature lets you not only visualize your targets and deadlines but change your targets based on changes in priority. Axio360 was made with continuous improvement in mind so that you can become cyber resilient.
To learn more, view our demo.



