Introduction
This article provides a single, comprehensive explanation of the National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity (NIST CSF) Informative References. It includes the :
- What the Informative References are
- How to use the Informative References
- Where to find the Informative References
- Overview of each Informative Reference included in V1.1 of the NIST CSF
- How to get Started with NIST CSF Today
What Are NIST CSF Informative References?
In the NIST CSF, Informative References are citations to related activities from other standards or guidelines. Their purpose is to provide additional information on how outcomes described in Subcategories may be achieved. There are multiple Informative References included for each Subcategory of the NIST CSF. All of the Informative References in V1.1 of the NIST CSF originate from six documents, but NIST recently created a website where additional or updated references can be downloaded. The documents included in the CSF and a link to the NIST website for additional references are included in the “Informative References included in NIST CSF Version 1.1” and “Additional Informative References Available through the National Cybersecurity Online Informative References (OLIR) Program” sections of this article. The Informative References from the first two Subcategories of the NIST CSF are shown in the rightmost column of the image below.
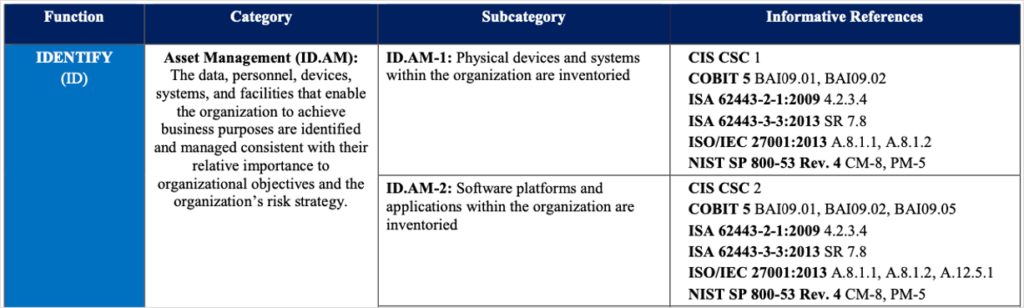
Image: NIST CSF Informative References for the first two NIST CSF Subcategories
How to Use the NIST CSF Informative References
Using Informative References to Achieve Desired Outcomes
To discuss how to use Informative References, it is important to first note two important aspects of NIST CSF Subcategories. NIST CSF Subcategories are the base unit of the NIST CSF. Put another way, they are the fundamental statements that make up the foundation of the NIST CSF. They are structured as short statements that describe particular outcomes of cybersecurity activities. For example, ID.AM-1 of the NIST CSF states that “Physical devices and systems within the organization are inventoried.” Subcategories do not prescribe the specific activities that may help achieve those outcomes. Informative References provide that additional detail—they provide examples of what organizations might do to achieve the outcomes described in each Framework Subcategory.
The way Informative References are used depends on the way the CSF is being applied by an individual user or organization. Those using the CSF in an informational context may need no more than an additional few sentences of explanation for certain Subcategories. An organization performing an in-depth implementation of some or all CSF Subcategories might choose to formally identify control statements from the Informative References, as well as from other references. This could be performed to help identify the actual cybersecurity activities an organization intends to implement as part of its cybersecurity program. An organization may go on to leverage selected Informative References to support governance and resourcing, cybersecurity program strategy, cybersecurity assessment, budgeting, and communicating with leadership.
Aligning Informative References to a Framework Profile
Developing Framework Profiles to describe the current state or the desired target state of specific cybersecurity activities is a key element of implementing NIST CSF. an organization plans to develop and implement a Framework Profile, Informative References should be aligned with and selected in support of that profile. In the case of an organization developing a Current Profile, Informative References may help in identifying which activities are in place that help achieve selected Framework Subcategories. In the case that an organization chooses to establish a Target Profile, selecting appropriate Informative References may aid in identifying appropriate controls to address differences between a Current Profile and a Target Profile. For more information on Framework Profiles, see Section 2.3 “Framework Profile” on page 11 of the
What to Avoid When Using Informative References
While the NIST CSF Informative References are intended to be useful, NIST provides specific guidance on their limitations. In general, NIST states in its “Informative References: What are they, and how are they used?” learning module that the Informative References are not intended to be exhaustive. Meaning that the documents that appear in the Informative References are not a complete list of documents where additional guidance may be obtained. NIST also states within the text of the CSF that the mappings between the CSF and the Informative References are not intended to be complete. The intent here is to communicate that each CSF Subcategory does not include an element from each informative reference and not all elements from each document are included in the NIST CSF Informative References. Additionally, and potentially most importantly, NIST states that use of the Informative References is not compulsory for Framework implementation. NIST goes on to say that organizations may choose to use different combinations of the Informative References, some but not all of them, or even different resources entirely to develop the right set of supporting resources for each organization’s situation and risk tolerance.
Where to Find the Informative References
The Informative References are a subcomponent of the NIST CSF Framework Core, which is one of three major components of the NIST CSF (the Framework Core, Implementation Tiers, and Framework Profiles). Within the Framework Core, Informative References are one of four subcomponents. The following table illustrates the four subcomponents of the Framework Core and where Informative References are located (see “Informative References” in the rightmost column below).
|
Functions |
|
Categories |
|
Subcategories |
|
Informative References |
|
IDENTIFY |
|
Subdivisions: Groups of outcomes |
|
Further subdivisions: Specific outcomes |
|
Informative References: Example methods to achieve |
|
|
|
|
||||
|
|
|
|
||||
|
|
|
|
||||
|
PROTECT |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
DETECT |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
RESPOND |
|
|
|
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
|
RECOVER |
|
|
|
|
|
|
|
|
|
|||||
|
|
|
|
||||
|
|
|
Table: Components of the NIST CSF Framework Core
For additional information on components and subcomponents of the NIST CSF, see NIST’s “An Introduction to the Components of the Framework” https://www.nist.gov/cyberframework/online-learning/components-framework. This article focuses on one subcomponent of the Framework Core—the Informative References.
Where to Find Informative References Included in V1.1 of the NIST CSF
There are six documents from which the Informative References were derived. Those documents are shown in the following table.
|
Informative Reference |
Link |
|
NIST SP 800-53 Rev. 4 |
nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf |
|
ISO/IEC 27001:2013 |
|
|
COBIT 5 |
|
|
CIS CSC |
|
|
ISA 62443-2-1:2009 |
This resource is no longer available from ISA’s website. Newer |
|
ISA 62443-3-3:2013 |
This resource is no longer available from ISA’s website. |
Table: List of Informative References included in NIST CSF Version 1.1
Additional Informative References Available Through the National Cybersecurity Online Informative References (OLIR) Program
In addition to the references included in Version 1.1, NIST leads the National Cybersecurity Online Informative References (OLIR) Program. This program is intended to extend the number of Informative References available to all users of NIST documentation by creating a standardized online catalog where anyone can submit a mapping of references from NIST documents. Several additional references are available in the Online Informative Reference Catalog for the NIST Cybersecurity Framework v1.1. It is important to note that NIST includes a disclaimer for these Informative References that they have not been reviewed by NIST for accuracy. As such, these documents should be reviewed prior to use to ensure they are appropriate for their intended application.
NIST Cybersecurity Framework v1.1 Informative Reference Overview
NIST SP 800-53 Rev. 4
Published by the U.S. National Institution of Standards and Technology, 2013
Description
NIST SP 800-53, as this is commonly called, is a comprehensive, detailed catalog of technical and nontechnical security and privacy controls. Revision 4 was published in 2013 [NIST 800-53 2013], a draft of revision 5 was published in August 2017 [NIST 800-53 2017], and the final public draft of Revision 5 was released in March 2020. Although SP 800-53 was developed originally for use in the U.S. federal government, it has gained widespread use globally by all kinds of organizations.
In addition to the control catalog, SP 800-53 provides guidance about risk management, security control specification and selection, and baseline security controls for low-impact, moderate-impact, and high-impact information systems.
NIST SP 800-53 Revision 5 contains more than 1,500 controls organized into 20 families. Each control contains a control description, supplemental guidance, control enhancements and references (if applicable), and the priority and baseline allocation for the control and its enhancements. These are the security and privacy control families and their identifiers:
|
AC |
Access Control |
MP |
Media Protection |
|
AT |
Awareness and Training |
PA |
Privacy Authorization |
|
AU |
Audit and Accountability |
PE |
Physical and Environmental Protection |
|
CA |
Assessment, Authorization, and Monitoring |
PL |
Planning |
|
CM |
Configuration Management |
PM |
Program Management |
|
CP |
Contingency Planning |
PS |
Personnel Security |
|
IA |
Identification and Authentication |
RA |
Risk Assessment |
|
IP |
Individual Participation |
SA |
System and Services Acquisition |
|
IR |
Incident Response |
SC |
System and Communications Protection |
|
MA |
Maintenance |
SI |
System and Information Integrity |
For additional information on the NIST CSF Informative References from NIST 800-53, please see Using NIST 800-53 to Interpret NIST CSF.
ISO/IEC 27001:2013 Information technology — Security techniques — Information security management systems — Requirements
Published by the International Organization for Standardization (ISO), 2013
Description
ISO 27001 or ISO/IEC 27001, as this is commonly called (IEC is the International Electrotechnical Commission), is an international information security standard that provides “requirements for establishing, implementing, maintaining and continually improving an information security management system.” “This International Standard can be used by internal and external parties to assess the organization’s ability to meet the organization’s own information security requirements” [ISO/IEC 2013]. It must be purchased from ISO.
The standard contains the following sections:
- Context of the organization
- Leadership
- Planning
- Support
- Operation
- Performance evaluation
- Improvement
- Annex A: Reference control objectives and controls
A good view of the complete set of ISO 27001 controls can be obtained without purchasing the standard by consulting the mapping of the NIST 800-53 controls to the ISO 27001 controls in Appendix I, “International Standards: Control Mappings for ISO/IEC 27001 and ISO/IEC 15408” of NIST 800-53 revision 5 [NIST 800-53 2017].
Certification of compliance with ISO 27001 is available through accredited certification bodies. For example, Amazon Web Services states that their certification is performed by an independent third-party auditor that is a member of the International Accreditation Forum [AWS 2019].
COBIT 5 and COBIT 2019
COBIT 5 was published by the organization formerly known as the Information Systems Audit and Control Association, ISACA, 2012
COBIT 2019 was published by ISACA in 2018
Note Regarding COBIT Versions
COBIT 5 was developed in 2012 and is the informative reference included NIST Version 1.1. COBIT 5 has since been updated to a new version titled COBIT 2019. An updated mapping of NIST CSF to COBIT 2019 is available from the NIST Online Informative Reference Catalog.
Description
Control Objectives for Information Technologies (COBIT) was designed as a framework for the Enterprise Governance of Information Technology (EGIT) and management of Information Technology (IT). It is not a cybersecurity model, but it includes foundational elements required to design and operate a mature cybersecurity program. COBIT 2019 includes the following domains:
- Evaluate, Direct and Monitor (EDM)
- Align, Plan and Organize (APO)
- Build, Acquire and Implement (BAI)
- Deliver, Service and Support (DSS); and
- Monitor, Evaluate and Assess (MEA)
COBIT was initially designed to aid in the audit of enterprise information systems but has since evolved into a full suite of products that can fulfill a number of functions surrounding IT, such as governance, strategic planning, control assessment, and program design.
Center for Internet Security (CIS) Critical Security Controls for Effective Cyber Defense Controls (CSC), Version 6 and Version 7
CIS Controls Version 6 was published by the Center for Internet Security (formerly by SANS) in 2015
CIS Controls Version 7 was published by the Center for Internet Security in 2019
Note Regarding CIS Control Versions
CIS Controls Version 6 is the Informative Reference included NIST Version 1.1. The Center for Internet Security CSC was later updated to Version 7. An updated mapping of NIST CSF to CSC Version 7 is available for download from the CIS website.
Description
The CIS Controls comprise 6 Basic controls, 10 Foundational controls, and 4 Organizational controls. Each of those contains sub-controls, with a total of 171 sub-controls [CIS 2019]. The controls are further categorized by Security Function: Identify, Detect, Protect, and Respond. For example, this is the first control (with control descriptions omitted):
- Inventory and Control of Hardware Assets
|
|
Asset Type |
Security Function |
Title |
|
1.1 |
Devices |
Identify |
Utilize an Active Discovery Tool |
|
1.2 |
Devices |
Identify |
Use a Passive Asset Discovery Tool |
|
1.3 |
Devices |
Identify |
Use DHCP Logging to Update Asset Inventory |
|
1.4 |
Devices |
Identify |
Maintain Detailed Asset Inventory |
|
1.5 |
Devices |
Identify |
Maintain Asset Inventory Information |
|
1.6 |
Devices |
Respond |
Address Unauthorized Assets |
|
1.7 |
Devices |
Protect |
Deploy Port Level Access Control |
|
1.8 |
Devices |
Protect |
Utilize Client Certificates to Authenticate Hardware Assets |
The CIS Controls are available for free download (in an Excel file) under a Creative Commons non-commercial use license. CIS provides companion guides for use of the controls [CIS CG 2019]:
- CIS Risk Assessment Method – A free method for self-assessment against the CIS Controls, with “instructions, examples, templates, and exercises for conducting a cyber risk assessment”
- CIS Controls V7 Measures & Metrics
- Mappings of the CIS Controls to other cyber security frameworks and standards
- A guide for applying the CIS Controls in industrial controls system environments
- A guide for small and medium-sized enterprises “to help them protect their businesses with a small number of high priority actions based on the CIS Controls”
CIS provides other resources, such as tools, communities, benchmarks, services, and educational materials. The CIS Controls FAQ gives information about who created the controls (an international consortium), how they are updated, what the relationship is between the Controls and other cyber security standards, who has endorsed the Controls, and who is using them (“thousands of global enterprises, large and small”) [CIS FAQ 2019].
ANSI/ISA 62443 Standards
American National Standards Institute/International Society of Automation (ANSI/ISA)-62443-2-1 (99.02.01)-2009 Security for Industrial Automation and Control Systems: Establishing an Industrial Automation and Control Systems Security Program was published by the ANSI/ISA in 2009
ANSI/ISA-62443-3-3 (99.03.03)-2013, Security for Industrial Automation and Control Systems: System Security Requirements and Security Levels was published by the ANSI/ISA in 2013
Notes on Reading the Names of ANSI/ISA 62443 Standards
ANSI/ISA 62443 includes several standards focused on the security of industrial systems. It was originally called the ISA-99 set of standards, and was renamed in 2010 to ANSI/ISA 62443. The format of the names for these documents has changed as the standards have evolved. The ANSI/ISA 62443 standards documents referenced in NIST CSF V1.1 use the naming convention outlined in the following table.
|
ANSI/ISA-62443-3-3 |
|||||
|
ANSI/ISA |
62443 |
3 |
3 |
(99.03.03) |
2013 |
|
Governing body name |
Set of standards |
Category number |
Standard number |
Previous ISA-99 document number |
Year published |
Later versions of ANSI/ISA 62443 standards do not include the parenthetical reference to the previous the ISA document number noted in the table above (e.g., “(99.03.03). Additionally, ANSI/ISA standards accepted by the International Electrotechnical Commission (IEC) or other standards institutions may be named with different institution name prefixes (e.g., “IEC 62443-3-3) in place the ANSI/ISA designation.
Description
The ANSI/ISA 62443 standards are intended to guide the development and implementation of secure Industrial Automation and Control Systems (IACS) and industrial communication networks. ANSI/ISA 62443-2-1 focuses on programmatic considerations for the management of cybersecurity within IACS such as personnel, policies, and procedures. ANSI/ISA 62443 includes a full suite of standards documents covering 4 categories:
- General
- Policies and Procedures
- System
- Component
The full list of current standards and those planned for future inclusion in 62443 standards is shown in the following image.
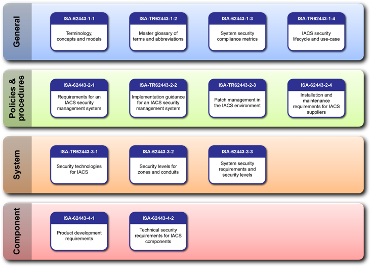
List of Current and Planned ANSI/ISA Standards
Image source: https://upload.wikimedia.org/wikipedia/commons/9/97/ISA-62443_Standard_Series_2012.png
How to Get Started with NIST CSF Today
The Axio360 platform is the easiest and fastest way to get started with NIST CSF. With the considerations above, you are well on your way to optimizing your work-from-home cyber program. If you’d like to learn more information and dive into more detail on how to perform a NIST CSF assessment in Axio360, you can book a demo.
Get started today with your NIST CSF assessment for free.
About the author: John Fry is Axio’s Director of Cyber Risk Engineering
Sources
[AWS 2019]
Amazon Web Services, “ISO/IEC 27001:2013,” 2019. https://aws.amazon.com/compliance/iso-27001-faqs/
[CIS CG 2019]
Center for Internet Security, “CIS Controls Companion Guides,” 2019. https://www.cisecurity.org/controls/cis-controls-companion-guides/
[CIS FAQ 2019]
Center for Internet Security, “CIS Controls FAQ,” 2019. https://www.cisecurity.org/controls/cis-controls-faq/
[ISO/IEC 2013]
International Organization for Standardization and International Electrotechnical Commission, ISO/IEC 27001:2013 Information technology — Security techniques — Information security management systems — Requirements, 2013. https://www.iso.org/obp/ui/#iso:std:iso-iec:27001:ed-2:v1:en
[NIST 800-53 2013]
National Institute of Standards and Technology, Security and Privacy Controls for Information Systems and Organizations, Rev. 4, NIST Special Publication 800-53, April 2013. https://csrc.nist.gov/publications/detail/sp/800-53/rev-4/final
[NIST 800-53 2017]
National Institute of Standards and Technology, Security and Privacy Controls for Information Systems and Organizations, Rev. 5, NIST Special Publication 800-53, August 2017. https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/draft




