Cybersecurity Capability Maturity Model (C2M2) Background
The Cybersecurity Capability Maturity Model (C2M2) contains a set of common cybersecurity practices that can be used to evaluate, prioritize, and improve cybersecurity capabilities. As a maturity model, C2M2 includes practices that range from foundational ones that are considered basic cybersecurity activities to those that are more advanced in terms of either technical sophistication or consistency and repeatability. This enables use of C2M2 to understand the current state of a cybersecurity program and track growth over time.
The C2M2 that is available today from the C2M2 Program of the United States Department of Energy’s Office of Cybersecurity, Energy Security, and Emergency Response website1 is a derivative of the Electricity Subsector Cybersecurity Capability Maturity Model (ES-C2M2) Version 1.0, which was first published in 2012. ES-C2M2 Version 1.0 was developed in support of a White House initiative to improve the cybersecurity of critical infrastructure organizations. The development project was led by the United States Department of Energy in partnership with the Department of Homeland Security and in collaboration with cybersecurity and maturity model experts from across the energy sector.
The model was built upon and tied together a number of existing cybersecurity resources and initiatives. Additional input to the model content was based on a review of cyber threats to the electricity subsector that the development team conducted to help ensure the model’s relevance. The initial draft of the model was revised after feedback was received from more than 40 industry experts and 17 pilot evaluations. The electricity subsector widely adopted the model and provided more feedback for improvements. Version 1.1 of ES-C2M2 was published in February 2014. The first derivative of the ES-C2M2, the Oil and Natural Gas Subsector C2M2, was developed along a similar timeline by replacing the Electricity–Subsector-focused examples with ONG-specific ones. The United States Department of Energy developed the next derivative of the ES-C2M2, the Cybersecurity Capability Maturity Model, by removing sector-specific references and terminology.
C2M2 is available for free in the Axio360 platform. Interested? Sign up at learn.axio.com/free-tool
C2M2’s Maturity Model Elements
The C2M2 is a maturity model, that is, it is “a set of characteristics, attributes, indicators, or patterns that represent capability and progression in a particular discipline.”2 These are some of the elements and concepts that make the C2M2 a maturity model:
- Cumulative progress expressed through maturity levels –In C2M2, progress is represented by maturity indicator levels (MILs). MILs provide a structure for attainment of increasing completeness, technical sophistication, and institutionalization of cybersecurity practices. The MILs are cumulative within each domain in that to attain a MIL in a given domain, all of the practices in that level must be fully implemented, and to move up a level, all of the practices in lower levels must be attained.
- Institutionalization – This has to do with performing cybersecurity activities consistently and the ability to sustain those activities over the long term. In C2M2, institutionalization is the focus of the Management Activities objective in each domain, which includes practices such as having adequate resources for the domain’s activities, using up-to-date policies, and assigning responsibility and authority for the performance of the domain’s activities.
- Process improvement focus – Maturity models are intended to help organizations evolve to more comprehensive, deliberate, and effective management of certain capabilities through planned improvement. Like other maturity models, C2M2 is structured to enable options for the scope of improvement—a single aspect of cybersecurity such as incident management, for example, or a broad view that aims for a specific MIL in all 10 domains. The “Using the Model” section of the C2M2 document can be used to guide a process improvement approach.
- Holistic focus on people, process, and technology – Another aspect of maturity models is that they look beyond solutions that are solely focused on technology to encompass the relationships among people, process, and technology that are necessary to make cybersecurity activities repeatable, manageable, and improvable.
See the “Maturity Models” section of the C2M2 document for more details about the maturity model aspects of C2M2.
Components of the C2M2
Domains
The model is organized into 10 domains, which are logical groupings of cybersecurity practices.
These are the domains in the current version of the model:
- Risk Management – Creating a risk management strategy; identifying, analyzing, and managing risk
- Asset, Change, and Configuration Management – Keeping inventories of information technology, operational technology, and information assets; establishing configuration baselines for assets; evaluating and logging changes to assets
- Identity and Access Management – Provisioning and deprovisioning identities for asset users; granting and revoking access; managing privileges
- Threat and Vulnerability Management – Identifying and responding to threats; identifying and reducing vulnerabilities
- Situational Awareness – Performing logging and monitoring; collecting information about the organization’s current state of cybersecurity; communicating the current state of cybersecurity to stakeholders
- Information Sharing and Communications – Fulfilling cybersecurity reporting obligations; sharing cybersecurity information with internal and external stakeholders; participating in information sharing and analysis centers
- Event and Incident Response, Continuity of Operations – Detecting, analyzing, and escalating events; responding to incidents; maintaining and exercising incident response plans; sustaining operations during incidents; recovering from incidents
- Supply Chain and External Dependencies Management – Identifying important customer and supplier dependencies; managing risks due to dependencies; establishing cybersecurity requirements for suppliers
- Workforce Management – Assigning responsibility for cybersecurity activities; conducting personnel vetting; training cybersecurity personnel; providing cybersecurity awareness activities for all personnel
- Cybersecurity Program Management – Creating a cybersecurity program strategy and program; obtaining sponsorship for the cybersecurity program; establishing a cybersecurity architecture; performing secure software development
Objectives and Practices
Within domains, cybersecurity practices are organized into groupings of related practices called objectives. The objectives in the Asset, Change, and Configuration Management domain, for example, are Manage Asset Inventory, Manage Asset Configuration, and Manage Changes to Assets. One of the objectives in each domain is called “Management Activities”; it contains practices that describe institutionalization activities. Those practices are similar across domains.
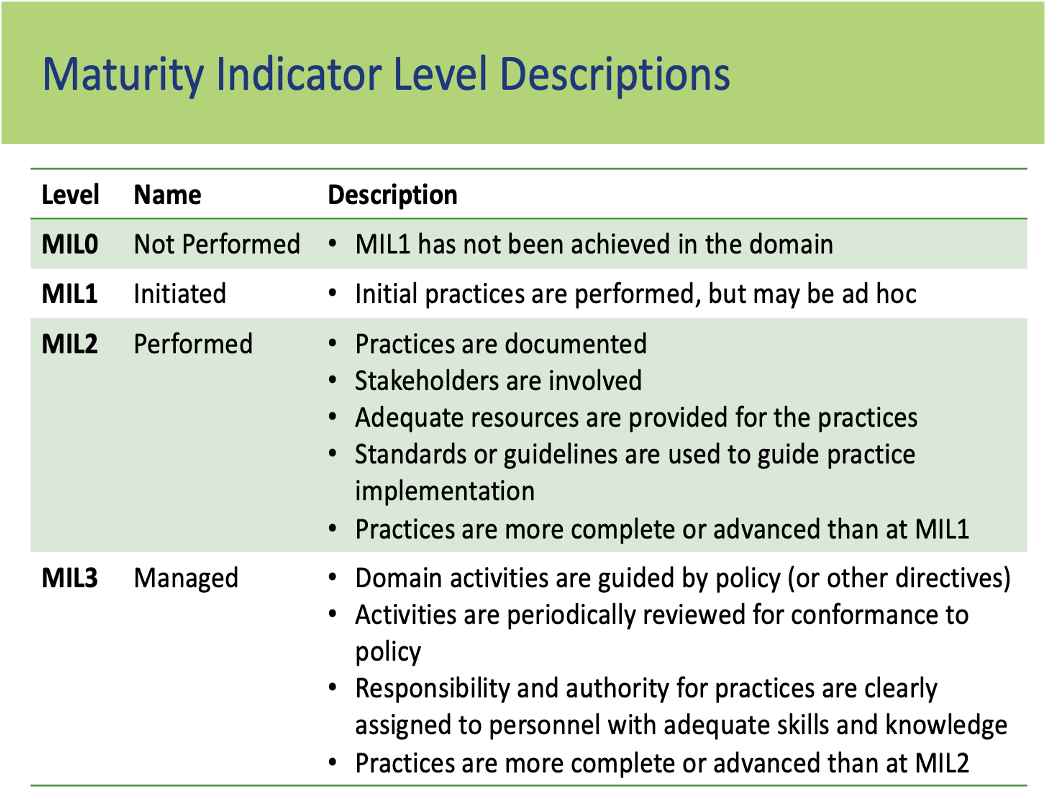
Maturity Indicator Levels
Within objectives, practices are grouped by maturity indicator levels (MILs). In Management Activities objectives, MILs define a progression of institutionalization; in the other objectives, MIL progression means that the practices become more complete in their implementation or more advanced in the way they are performed.
These are the four MILs in C2M2:
- MIL0 means that the practices at MIL1 have not been implemented. All of the MIL1 practices in a domain must be implemented to achieve MIL1 in that domain; therefore, as long as even one of the domain’s MIL1 practices has not yet been implemented, the organization is at MIL0 in the domain.
- MIL1 represents the basic cybersecurity activities that any organization should perform. The C2M2 Foundations Assessment in Axio360 is a wizard-style questionnaire that enables a quick determination of whether MIL1 has been attained.
- MIL2 practices are progressively more complete, advanced, and ingrained in the way the organization operates. These are the model’s intermediate practices.
- MIL3 practices are more complete, advanced, and ingrained than MIL2 practices; MIL3 practices are also tightly connected to the organization’s risk management program. These are the model’s advanced practices.
Attaining MIL1 in all 10 C2M2 domains is a reasonable goal for development of a cybersecurity program. Beyond that, a target of MIL2 or MIL3 can be set for each domain based on an understanding of the organization’s risk tolerance and threat environment, and also on an evaluation of the anticipated benefits of implementing the practices that would be required to achieve the target. In Axio360, a target MIL can be set for each practice.
Who Can Benefit from Using the C2M2?
The United States Department of Energy created the C2M2 for energy sector and other critical infrastructure organizations, and the model has had wide adoption among such organizations. However, C2M2 Version 1.1 practices are written in a style and at a level of abstraction that enables them to be easily interpreted for any type of organization, including those of any structure and size.
Ready to Get Engaged?
Cybersecurity leaders can easily be consumed by the constant firefighting inherent to the cybersecurity trade—both incident-driven and project-related. You may be committed to implementing a proactive strategy for your cybersecurity program but be constantly thwarted by never-ending distractions. An effective way to quickly develop your strategy and get the wheels in motion is what’s needed to enable you to focus on what matters most and maybe even have some time to think about what’s next.
You can implement C2M2 using a planning technique called Scripts and Rhythms to quickly plan your cyber program activities and make sure those activities actually happen.
To learn more about the C2M2, view a demo of the Axio360 platform and see C2M2 in action.
[1] The United States Department of Energy Cybersecurity Capability Maturity Model
https://www.energy.gov/ceser/energy-security/cybersecurity-capability-maturity-model-c2m2-program
[2] The United States Department of Energy Cybersecurity Capability Maturity Model
https://www.energy.gov/ceser/energy-security/cybersecurity-capability-maturity-model-c2m2-program
C2M2 is available for free in the Axio360 platform. Interested? Sign up at learn.axio.com/free-tool




