Why you need one, what to look for, and how to get started
Are you still relying on the outdated governance, risk, and compliance (GRC) method for managing your company’s cyber risk? If so, you have essentially no visibility into your organization’s real financial exposure.
In today’s world, your leadership needs to know how and where to invest to minimize their risk effectively. The only way to get these answers is with an integrated risk management platform.
If you are struggling with disconnected spreadsheets, a lack of visibility, and poor communication, you need to move toward an integrated risk management approach to take action and improve your organization’s cyber posture. In this blog post, we will present a beginner’s guide to integrated risk management platforms to help someone just getting started, enabling them to deliver clarity and measurable value to their cyber risk program.
Why do you need an integrated risk management platform?
There is now a hacker attack every 39 seconds. And the risk is only growing. The FBI has seen a 300% increase since the start of the COVID-19 pandemic in the number of cybersecurity complaints its Internet Crime Complaint Center receives. This is in addition to the massive SolarWinds cyber attack, an unprecedented breach that experts are still scrambling to understand. The unprecedented nature of the attack has also presented challenges in understanding insurance coverages. “Am I Covered or Not?” is a common question we get asked by our clients. We even had the privilege to host a fireside chat with some of the world’s leading experts on the matter.
So, what does this dramatic increase in cyber-attacks mean for your organization specifically? If you work at a publicly traded company, the average cost of a cyber breach is $116 million. An Accenture study on the cost of cybercrime estimated that a total of $5.2 trillion is at risk globally over the next five years. And in a separate report, Accenture found that “choosing the wrong strategy to invest in cybersecurity technologies can cost the organization far more than inefficient utilization of resources; it can damage an organization’s brand, reputation, and future prosperity.”
You are also up against ever evolving regulations and standards. For example, companies that must comply with the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) requirements often find themselves scrambling to keep up and paying huge fines when they can’t comply. For more information about compliance firefighting, you can watch with our trusted partner, Archer Energy Solutions.
To prepare for and proactively protect against today’s sizeable and increasing cyber threats, you need to establish a standard way of demonstrating your company’s cybersecurity maturity to all stakeholders before an attack happens. And you must be able to answer the question: When an attack happens, do we have the capability to continue operating as a business? To do this, you need an integrated risk management (IRM) platform.
What is an integrated risk management (IRM) platform?
An integrated risk management (IRM) platform gives you:
- A permanent home for recording all your cybersecurity program initiatives
- Insight into all potential risks and their associated costs
- A clear view of your compliance landscape and how it impacts the business
- Flexibility to assess your cyber posture amid continuously changing standards and threats
In addition, IRM platforms enable you to:
- Demonstrate compliance for regulators
- Prioritize the most important decisions for technology initiatives
- Report what matters to non-cyber savvy stakeholders in clear terms
Gartner’s definition of an IRM platform is “a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks.” But how does that break down into real-world practical applications?
How does an IRM differ from governance, risk, and compliance (GRC)?
If you are still relying on a GRC approach, you are failing to see the full picture. GRC is focused almost entirely on compliance. “The problem with GRC is all C, no G, no R,” according to one Axio client, a CISO of a Fortune 100 company responsible for safeguarding both digital assets and mission-critical infrastructure.
IRM takes compliance into account, but approaches cyber risk more broadly, looking across the company at exposure and business impact. An IRM approach synthesizes information from disparate sources to give you a . IRM “enables simplification, automation and integration of strategic, operational and IT risk management processes and data,” according to Gartner. Here is Gartner’s list of key differences:
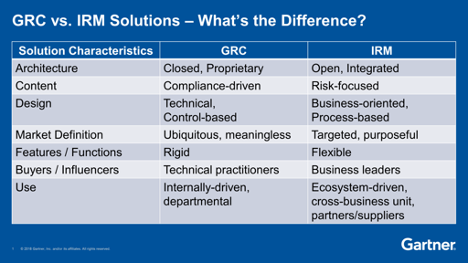
An IRM platform measures your cyber risk exposure and manages your cybersecurity program in a defensible and holistic way.
The proof is in the pudding, and when the time comes to present objective security information an IRM can save the day. From high-pressure conversations in the boardroom, to split-second decisions in the Security Operations Center, an undisputable view of cyber risk must be presented transparently, both from a bird’s eye view to the most minute micro level of detail.
Integrated and ecosystem-driven: An IRM platform will allow you to look at cyber risk across your entire organization as well as at your vendor and third-party relationships. IRM breaks down siloes to empower you to see where your greatest exposure is and how to improve your controls to reduce or eliminate that risk.
Especially after the SolarWinds attack, understanding the web of intricate third-party exposure is becoming a priority for security leaders. An IRM platform can easily house models that help one understand their supply chain and vendor risk. For example, the National Institute of Standards and Technology, more commonly known as NIST has developed many models in addition to their most popular one, the CSF, such as the 800-53 and 800-171, specifically designed in helping better understand supply chain and third-party vendor risk.
Risk-focused: Moving from a control-or compliance-based program (GRC) to a risk-based program (IRM) helps an organization apply resources to the highest-priority areas. A risk-based view is forward looking and provides an organization with loss scenarios that may or may not materialize.
Targeted: An IRM helps you decide which controls—financial, technical, physical, administrative—to prioritize for investment and when it makes financial sense to accept risk. For example, Axio’s IRM platform lets you assess your controls through its Controls Initiative. The Control Initiatives method allows companies to play out how changing one or more controls would affect their exposure. You can evaluate how much of the risk that is inherent to a cyber loss scenario you could reduce by changing a control. Additionally, you can consider how much additional risk they would be taking on if you were to reduce their controls.
Business-oriented and built for business leaders: Another essential part of an IRM platform is cyber risk quantification. The only way for organizations to understand how cyber events could impact their bottom line is by calculating the potential financial costs of—or quantifying—their risk. Today, most organizations are not quantifying what a security incident would cost their organizations.
Every organization needs to understand its risk scenarios in the context of achieving its business strategy and objectives. By embracing an IRM approach that includes cyber risk quantification, you are successfully replacing laundry lists of security to-dos with necessary next steps aligned to the risk, in dollars and cents. You will be moving to a forward-looking view, greatly strengthening your cyber posture.
What are integrated risk management (IRM) software and solutions?
An IRM platform must address the two main areas of cyber risk management:
- Assessment and planning
- Quantification and analysis
The platform must do what the name implies—integrate these areas to give you a comprehensive and strategically-linked cyber risk playbook.
Cybersecurity Assessment and Planning
Assessment and planning should encompass an ongoing assessment process, internal and external benchmarking, improvement planning and tracking, as well as reporting. An integrated risk management platform still allows you to complete the compliance assessments that matter to you but gives you the ability to do so more quickly—and makes them actionable. The platform should empower you to see how changes and improvements to your compliance will impact your company.
Features to look for in an IRM platform include:
- Pre-loaded with some of the most popular frameworks such as NIST CSF, C2M2, CIS20, and CMMC for rapid assessments
- Alternately, the ability to import any compliance framework or maturity model regardless of industry and/or use case
- Rapid assessment scoring to set a baseline of how you are doing
- Saving and tracking of all your assessments in one easy to access place
- Memorializing of improvement milestones to track progress as you make improvements
- Assigning of action items and notes to colleagues through the system
- Setting of a target to see how your current state stacks up
- Comparing of your program to internal and external benchmarks
- Generating a roadmap for your cybersecurity improvements
- Producing rich reports for the board and other stakeholders
Cyber Risk Quantification and Analysis
Quantification enables you to analyze the unique risks to your business and calculate how individual risk scenarios would impact the bottom line. An IRM platform should make it easy for you to model potential cyber risk scenarios and calculate the cost of these potential scenarios to your business.
The platform should help you identify all relevant, potential cyber risks across business units and threat vectors that you may not have previously considered. Threats you do not even realize you are at risk of are a major problem. Accenture has found that “40 percent of security breaches are now indirect, as threat actors target the weak links in the supply chain or business ecosystem.”
You should also be able to estimate all-in costs of exposure—including from indirect attacks—and evaluate how specific controls and mitigations will reduce your risk.
IRM platforms must also help you determine what kinds of risk are worth prioritizing.
Anecdotally, Axio worked with a security leader who was losing sleep over understanding the cost of a cyber risk scenario if it would materialize. It wasn’t until she saw the quantified results in the Axio360 platform, that she realized the maximum-expected loss could be tolerated by the business.
How do you implement an integrated risk management program?
Get Internal Buy-In
Moving from the old GRC approach to a modern IRM program requires a significant organizational realignment in terms of how to manage cyber risk. An IRM approach will call for strong involvement and buy-in from your company’s executive leadership and board.
You can begin with your CISO by asking him or her these four questions:
- Do we know our risk and fully understand the dollars and cents involved? Have we taken a sampling of scenarios, put various operational and functional staff around a table and used their collective knowledge to estimate what each of a variety of events could cost?
- Do we use a maturity-based cyber evaluation framework and align it with the scenarios quantified in the previous step?
- Do we maintain the resources and financial ability to recover from a meaningful event? Do we have the right balance of financial reserves and insurance to pay for as much (or all) of the forensics costs, notification requirements, lost revenue, stolen funds, legal fees and liabilities, repair costs or replacement of damaged assets and others? How do we understand how much insurance to buy? See Step 1.
- Do we benchmark our organization against others, possibly a peer group? You don’t need to have a the best cyber maturity, as hackers often will look for and exploit the weakest targets when hunting for new victims.
Test Drive Options
You need an IRM platform that fits your business. Axio makes it easy for you to quickly test its integrated risk management platform. You can get instant access to the platform and see how you can improve your company’s cyber posture in just 48 hours.
When test driving IRM platforms, look for a system that:
Is easy to use: Try out different aspects of the IRM platform to make sure the user interface is intuitive and efficient.
Has in-depth reporting: Make sure the IRM platform can produce the types of reporting you need (and can so do efficiently) to satisfy all stakeholders.
Can be implemented quickly and easily: You want an IRM platform that will allow you to hit the ground running. You need to be able to start managing risk from day one, not months down the line.
When deciding which IRM platform, be weary of solutions that take months of complicated set up, as well as pricey consulting support to enable onboarding. There’s never guarantee that you will enjoy the fruits of all the involved labor you paid for.
Make the Shift in Your Thinking and Approach
You can start to shift your organization toward an IRM approach by identifying the mission-central parts of the business that could be impacted by a cyber event. These are the company’s essential functions —the things that keeps the lights on and business flowing that are exposed to a cyber event. By identifying what is most important to achieving the company’s mission and creating value for customers, you will be able to narrow down the people, processes, and technology you need to focus on when you implement your new integrated risk management platform. The goal is to identify the ways a hacker could use technology to steal your company or disrupt its business through targeted or opportunistic attacks.
This business-value centric approach also ensures that team members from across your company play a role in managing cyber risk. Instead of a sole cybersecurity or IT department putting controls in place, leaders from every unit weigh in on what business operations—and outcomes—the company needs to prioritize.
The shift from subjective risk ratings owned by the cybersecurity team to business-centric risk analysis with broad stakeholder involvement is a major change. You will need an integrated risk management platform partner that can advise and assist you in shifting your company’s thinking and way of approaching cyber risk.
Implement IRM Software
Once you have the buy-in and you have aligned internal stakeholders around the IRM approach, you are ready to fully implement an IRM software platform. Implementation will require:
Training users: Implementing any new software requires onboarding and training. The same is true of an IRM platform.
Migrating data: Depending on what information you have in existing systems; you will likely need to migrate at least some data from your old system to the new IRM platform. The best way to do this is through APIs. Axio360 has restful APIs that can be used for integration to push and pull data from other systems in the organization.
Determining future risk software ecosystem: For organizations that have specific compliance obligations and have a lot of legacy compliance data, there may be a need to continue to use both a legacy GRC system in addition to an IRM platform. These platforms may need to coexist and feed data to one another.
Next Steps to Ensure Success
Once you start working toward implementing an IRM platform, you should immediately start to think through use cases. You want to determine what if any kind of evolution might be necessary in your strategy and how you communicate about security in the organization. One of the most important values of a good IRM platform is its output. The simplification of security reporting and understanding of not only the current state, but where the company needs to go, can:
- Get budgets approved faster
- Initiate projects with greater energy and collaboration
- Provide confidence that security and risk orgs are driving towards the best destination while firing on all cylinders, on the best road, without wasting a drop of fuel.
How One Energy Utility Company Made a Change to an IRM Platform
A major Energy Utility company discovered compliance assessments were not enough. They worked with Axio to move to an IRM approach.
The Energy Utility realized that compliance assessments were not giving them a true picture of their risk. The CSO concluded that the security team did not have the information they needed to stand behind what they were presenting to their board. Compliance assessments are binary tests for the presence of specific controls. The presence of certain controls does not necessarily indicate that the company has mitigated a risk. And the absence of a control does not indicate a risk is present that the company needs to mitigate. What the Energy Utility wanted was a risk view that spanned their organization at an appropriate level of resolution. They also wanted a view of risk that they could be aggregated for the board in one report and would allow them to speak to their entire company using a single risk frame. The CSO wanted to transition from a control and compliance centric security strategy to a risk-based security strategy.
They purchased Axio360, Axio’s IRM platform. Axio worked directly with their CSO. The CSO wanted to be able to plan and track improvements associated with the organization’s cyber risk posture. The company also needed to harmonize the assessment basis they were using for tracking their control implementation progress. Previously, they had been looking at projects using multiple different assessment systems. The CSO wanted a a single system to use as a common thread to look at everything in a consistent way to do apples to apples comparisons across the organization’s systems and business processes. Finding a common language was a key need for this CSO. Making the most appropriate cybersecurity decisions is often hindered by the lack of clear communication due to various levels of knowledge domains. While some leaders may feel more comfortable in technical jargon, others are only adept and more financially based metrics and KPIs.
The Energy Utility was able to begin work in Axio360 immediately upon implementation. Within days of signing a contract with Axio, the Energy Utility was able to start using their new IRM platform. Axio supported the initiative with training and onboarding. The company rolled out the IRM platform with training across multiple business units. Axio provided a range of low-touch training sessions combined with more hands-on guided workshops. Deploying a variety of training approaches and rolling them out in parallel empowered the company to make sure different stakeholder groups across the organization received the information they needed to start working in the platform as quickly as possible. The company also has a cross-team working group that shares information to ensure everyone is benefiting from effective implementation techniques. Axio’s product team attends these meetings to get feedback and make changes as needed to Axio360.
Stakeholder teams at the Energy Utility company are getting a much better sense of the role of security and cyber security risk within the overall operational risk landscape in the organization. Within weeks of being up and running, the company was able to start to map cyber risk into terms business units understand better. The company is starting to think about how to manage risks differently, and they are looking at specific systems that they did not realize previously were at risk.
Bottom Line
Cyber risk is a complex problem. But the solution does not have to be. You have to understand the risk landscape in which you operate. You also must know your own environment and continuously assess and manage the people, information, technology, vendors, partners, and suppliers upon which you are dependent to operate. The only way to do this is with an IRM platform.
Organizations cannot control many of the external conditions in the cyber risk landscape in which they operate, but by implementing an IRM platform they can control how they plan, manage, and direct resources to adapt, overcome, and improvise.



