In this blog post we expand on the issue of silent cyber we mentioned in our last blog and dive into different examples of insurance exclusions that may be present in your portfolio.
Understanding your broader insurance portfolio
Analysis is required to understand how a specific policy will respond to cyber as a peril.
What makes it challenging is that the treatment of silent cyber varies by choice of law. And from a global perspective, US courts have had tendencies to favor the insured while UK courts have favored insurers.

Exclusion language
Exclusion language varies by product and insurer. The typical language is structured in a way to first define what cyber risk is, and then exclude it from a particular policy. Some insurers have included wording that would first provide the definition of “affirmative” cover for cyber risk and then either grant the coverage with or without some limitations, such as sub-limits or zero out the limit as an effective exclusion.
Examples of Insurance Exclusions
Terrorism: typically excluded on property policies
- Definition from a property policy: Act(s) of terrorism means an act, including but not limited to the use of force or violence and/or the threat thereof, of any person or group(s) of persons, whether acting alone or on behalf of or in connection with any organisation(s) or government(s), committed for political, religious, ideological or similar purposes including the intention to influence any government and/or to put the public, or any section of the public, in fear.
- Exclusion from the same policy: Except as otherwise provided under the Additional Coverages, Additional Time Element Coverages or Global Coverage Extensions (and in such event, only to the extent provided therein), we do not insure for loss or damage caused directly or indirectly by any of the following. Such loss or damage is excluded regardless of any other cause or event contributing concurrently or in any sequence to the loss or damage. The following exclusions apply whether or not the loss event results in widespread damage or affects a substantial area:
- Loss, damage, cost or expense of whatsoever nature directly or indirectly caused by, resulting from or in connection with any act(s) of terrorism; and/or
- Loss, damage, cost or expense of whatsoever nature directly or indirectly caused by, resulting from or in connection with any action taken in controlling, preventing, suppressing or in any way relating to any act(s) of terrorism.
- Notwithstanding any exception in any other exclusion to the contrary, we do not provide coverage for any act(s) of terrorism, including any ensuing loss or damage.
CL380 (War) Exclusion
- Subject only to Clause 1.2 below, in no case shall this insurance cover loss damage liability or expense directly or indirectly caused by or contributed to by or arising from the use or operation, as a means of inflicting harm of any computer, computer system, computer software programme, malicious code, computer virus or process or any other electronic system.
- Clause 1.2 – Where this clause is endorsed on policies covering risks of war, civil war, revolution, rebellion, insurrection, or civil strife arising therefrom, or any hostile act by or against a belligerent power, or terrorism or any person acting from a political motive, Clause 1.1 shall not operate to exclude losses (which would otherwise be covered) arising from the use of any computer, computer system or computer software programme, or any other electronic system, in the launch and/ or guidance system, and/or firing mechanism of any weapon or missile.
NMA 2914 Exclusion (pertinent to energy property policies)
- This Policy does not insure, loss, damage, destruction, distortion, erasure, corruption or alteration of ELECTRONIC DATA from any cause whatsoever (including but not limited to COMPUTER VIRUS) or loss of use, reduction in functionality, cost, expense of whatsoever nature resulting therefrom, regardless of any other cause or event contributing concurrently or in any other sequence to the loss.
- ELECTRONIC DATA means facts, concepts and information converted to a form useable for communications, interpretation or processing by electronic and electromechanical data processing or electronically controlled equipment and includes programmes, software, and other coded instructions for the processing and manipulation of data or the direction and manipulation of such equipment.
- COMPUTER VIRUS means a set of corrupting, harmful or otherwise unauthorised instructions or code including a set of maliciously introduced unauthorised instructions or code, programmatic or otherwise, that propagate themselves through a computer system or network of whatsoever nature. COMPUTER VIRUS includes but is not limited to ‘Trojan Horses’, ‘worms’ and ‘time or logic bombs’.
- However, in the event that a peril listed below results from any of the matters described in paragraph a) above, this Policy, subject to all its terms, conditions and exclusions will cover physical damage occurring during the Policy period to property insured by this Policy directly caused by such listed peril.
- Listed Perils: Fire, Explosion (this list is often customized)
So many policies, so little time for understanding
A typical business may have over a dozen insurance policies in their portfolio. How can one be certain about their cyber strength?
Below is the simple 3 step process we use in the Axio360 Insurance Stress Testing
- Quantify the cyber risk scenarios pertinent to your business in dollar terms
- You get a financial view of your expected exposure per scenario from the worst case to best case impact.
- Aggregate all your insurance policies in one place and scan with machine learning
- You can rapidly identify problematic policy language indicating a lack of coverage
- Align Your Insurance Gaps with Your Quantified Risk Scenarios
- Partner with our analysts to assess recovery potential based on your insurance policies, contracts, and compliance with cybersecurity standards.

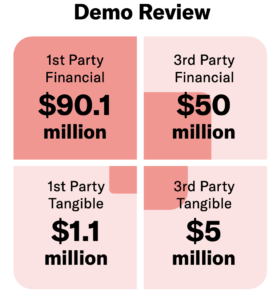
In the next few, final blog posts, we will conclude the series by looking forward in the world of cybersecurity and insurance, providing final recommendations to “ensure” you are properly insured.
To learn more about how you can truly understand your coverage don’t hesitate to reach out or book a meeting.





