It’s no secret that cybercriminals continuously test company networks and employees to seek out vulnerabilities. Hackers use every digital trick up their sleeves to steal data and, in some cases, even threaten to publicly release sensitive information. As the world has moved into an increasingly digital direction, ransomware attacks are growing sharply and causing more headaches than ever for companies.
The topic of ransomware and its impact on businesses is explored in a recent webinar from Axio, AIG, and Security Boulevard. Axio Co-Founder and President David White and AIG Cyber Product Lead Garin Pace spoke at length about the state of ransomware in 2021 and where things are likely headed in the future.
Below we will highlight some of the biggest insights from the conversation, including top ransomware trends and the evolution of sophisticated ransomware attack patterns.
2021: Ransomware Latest Trends (‘It’s Not Your Father’s Ransomware’)
As the world moved into an increasingly digital direction in 2020 due to the pandemic, cyber threats to companies also increased throughout the year. There was an average 139% year-over-year increase in ransomware attacks in Q3 of 2020 from Q3 of 2019. All sectors are impacted by ransomware and no industry was spared. For example, successful ransomware attacks on the education sector increased by an astounding 388% in the third quarter of 2020.
“It’s a plague on business,” Pace said. “This is not your father’s ransomware. Ransomware demands used to be in the hundreds of dollars, and the biggest loss was maybe some pictures or documents on your personal computer. Now these attacks, unfortunately, are crippling networks or stopping whatever a company is producing or stopping the flow of information. They are very significant incidents.”
During these attacks, not only are hackers out to hold data or networks hostage, but they are also often exfiltrating data and threatening to publish it elsewhere if companies don’t pay up. These attacks can also prove incredibly costly, with ransom demands averaging $5 million and topping out at $40 million. In an alarming example, Cognizant estimates the cost of its highly publicized April 2020 ransomware attack at between $50 and $70 million.
Data Exfiltration Rising as a Part of Ransomware Attacks
The threat of ransomware to companies continues to rise, but data exfiltration specifically is growing at an alarming pace. As of Q2 of 2020, about 50% of ransomware cases now include data exfiltration, which means things such as user names, passwords, and personal finance information have been stolen. While a company could have all of this data backed up, it can be incredibly damaging to have the stolen data released publicly by the hackers. Thus, they hold that for ransom as well, heightening the stakes.
“One of the more recent trends that we’ve seen started at the beginning of 2020 is not only the encryption of files and the ransoming back of the availability of the network but also exfiltrating data,” Pace said. “To increase the amount of leverage they have and to get the victims to pay their demands, they are not only ramping back the decryption key, but they are also exfiltrating the data and then threatening to publish it. They’re extorting victims as well. That’s, unfortunately, a trend that has started in 2020 and seems to be accelerating. So you should be aware that not only is ransomware a big threat to availability interruption, but all the risks that come attendant with data breaches also come into play increasingly, with liability, reputation damage, and regulatory risks.”
Surprise, Surprise Cyber Criminals Don’t Keep their Word
However, while many companies have bargained with hackers who performed data exfiltration tactics, there’s some indication we are at a tipping point. Coveware, for example, notes that many cybercriminals aren’t holding up their “end of the bargain” and released data even after receiving payments. As such, companies may not feel the need to pay for exfiltrated data because there’s no way to guarantee the deal will be honored, so to speak.
Ransomware Insurance Claims Show Increasing Severity
The cyber insurance market helps us reflect and understand the overall threat landscape. Ransomware, a large part of cyber insurance, has seen its frequency continue to rise. Ransomware tactics have evolved continuously and now pose a material risk to enterprises.
In the first half of 2020, insurers have seen 75% of the 2019 total of ransomware claims, so the scale is increasing. Ransomware has also increased its market share for the most significant losses that businesses see.
“Through Q3 of 2020, ransomware has only continued to grow in frequency,” Pace said. “In our data, I think it matches the greater the threat suite that companies see. Of course, we all read about it in the news, and it continues to impact not just the cyber insurance market but business at large.”
Insurers Play a Role in Addressing Ransomware Risk
In the 20th century, the insurance industry helped to drive safety and engineering standards in many industries. For example, insurance companies played a role in bringing down the risk of deadly boiler explosions. More recently, the insurance industry began providing financial incentives to address point-of-sale intrusions and credit cards being stolen. Today, following a similar path, insurers are working to understand and proactively address the impact of ransomware.
The insurers have what is often referred to the industry as “privileged visibility.” This means that they have much data and insights about the nature of the ransomware and can work closely with companies on solutions.
“Cyber insurers are some of the only organizations that have data on the cybersecurity posture of an organization before an event and detailed insights into what happened during an event and how the event occurred,” White said. “So they’re one of the few places in the world where you can really look for real data on the effectiveness of controls.”
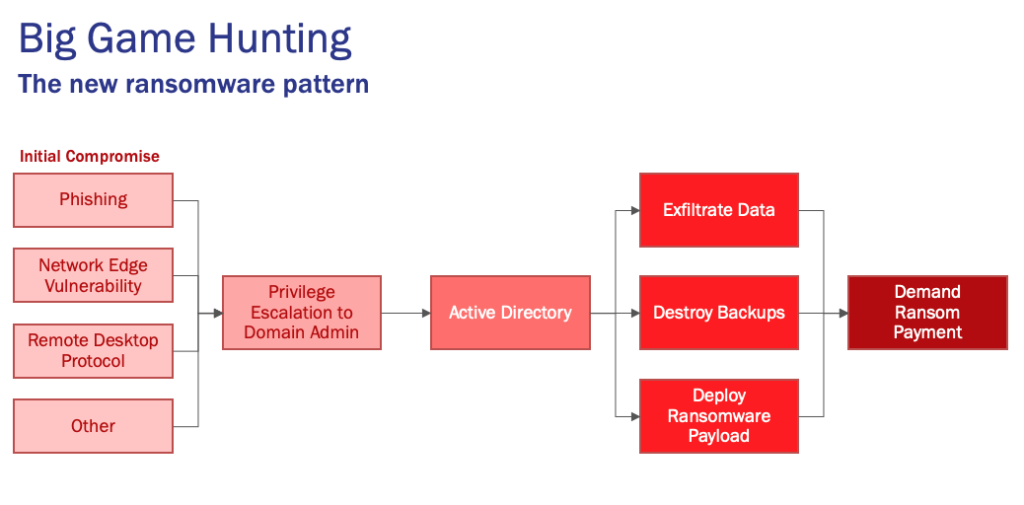
Evolution of Ransomware Attack Patterns (Big Game Hunting)
One other major trend that is important to understand about ransomware attacks in 2021 is that hackers and cybercriminals are engaging in “big game hunting,” a term popularized by cybersecurity firm CrowdStrike. In this new tactic, cybercriminals go deep into systems instead of, for example, just putting an attachment on a bunch of spam emails in hopes of getting someone to click accidentally. Those old-school attacks typically netted small ransoms, so instead, we see more coordinated and strategic ransomware deployment.
“Attackers are now going after the big game, they’re going after the entire network,” Pace said. “Where they are getting someone to click on a link using phishing as an entry point into the organization, their first thought is not to deploy ransomware. It’s to play a little bit more of a long game, escalate privileges, move laterally, do some reconnaissance, find the data, and then go after deploying ransomware not to a single computer but to as much of the network as they can.”
How Big Game Hunting Typically Starts
When a big-game-hunting incident occurs at a company, it starts with an initial compromise point. The three most common compromise points are:
- Phishing: This is when an attacker presents itself as someone they are not in an attempt to collect personal information, such as pretending to be your bank in an email in order for you to reveal your account numbers or password.
- Network Edge Vulnerability: Typically, this is when network equipment software has not been patched and had an exploitable vulnerability.
- Remote Desktop Protocol: Usually, this is when a remote desktop software tool that already has access to a machine is exploited and then uses the access to the device to steal information.
“Any company that is thinking about ransomware, and their resilience, should be looking at all three of these entry methods,” Pace said. “We’ll never stop all of these. But we want to certainly reduce the amount that’s coming into the top of the funnel.”
Cybercriminals Take Time to Collect Information and Obtain Admin Access
Once a hacker has exploited one of the common compromise points, they then take their time and methodically work. Pace notes that these hackers would have struck immediately in the past, but now they could take weeks to find out where everything is and understand how the systems work. But the ultimate goal most likely is to obtain administrator privileges, which lets them exploit computers all across the network.
After the network is compromised, hackers will work to exfiltrate data, destroy backups, and deploy more ransomware wherever it can go. Once all this is done, the hackers make their demands public and often threaten to release exfiltrated data or delete the only remaining copy of essential data.
Prepare for Uncertainty with Axio360
If your company requires more clarity on the risk of ransomware threats, Axio360 can provide a path forward. You can launch and complete a Ransomware Preparedness Assessment for free in the Axio360 platform. It’s a quick way to understand your current cyber posture and prioritize what critical improvements need to be done to improve as you move into 2021.




