In this next part of the blog series on the connection between cybersecurity and insurance, we will provide a basic overview of how insurance policies are structured from a financial perspective.
In the last blog, we covered the origins of insurance, but insurance has come a long way since then. Insurance policies have different structures and insurers often seek to reduce their own risk by spreading it to various types of insurers.
Modern insurance focuses on spreading the risk that needs to be protected.
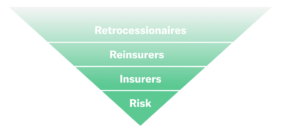
This inverse pyramid demonstrates how risk is transferred, from the first step of purchasing a policy, to spreading the risk to reinsurers and retrocessionaires. This structure allows insurers to provide coverage for a broader subset of buyers, as well as resell to other investors to minimize their risk and allow more entrants into the market.
The distinction between a SIR versus a deductible
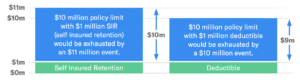
An important element of a modern insurance policy besides paying a premium, is how much risk the policy owner must bear. Above, the green section of the diagram shows two common policy structures. With a $1M deductible policy, the insurer pays for losses and then collects reimbursement afterwards, up to the amount of the deductible. With a $1M SIR (Self Insured Retention) in place, you’re required to make payments first and the insurer only begins to make payments once the SIR is satisfied.
The Insurance Tower
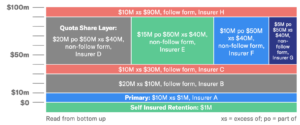
Organizations usually purchase large amounts of coverage because of the complex nature and scope of their business functions. Large limits are typically built from many layers from various insurers. Layers can be serial or parallel. These structures help insurers manage their risk. The price per unit of capacity typically drops at each layer. This is an example of a $100M policy.
Types of Insurance
Axio looks at risk through four quadrants. Cyber events can (and have) resulted in impacts in all four of these quadrants. This framework helps us think through and quantify the full range of potential impacts from cyber events. Because it aligns with insurance coverages, it can help us optimize our insurance portfolio for cyber.
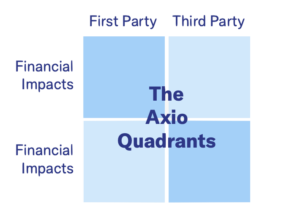
Financial Impacts: Affect Revenue and Expenses
Financial impacts are easy to calculate because they have a defined cost attached to them. Often, a customer data breach will result in financial impacts. In general terms a financial impact is one that means it can have an adverse effect on both P&L side of a financial statement as well as the balance sheet.
Tangible Impacts: Affect People and Property
Tangible impacts are more complex, they are the result of a chain reaction of a risk and often can only be calculated by examining the composition of the entire linkage that results from a cyber event. For example, if a production line is hacked, resulting in robotic systems assembling a ventilator machine improperly, there are now multiple third-party tangible impacts such as bodily injury and product liability.
Now that we have covered the basic concepts of insurance and the types of policies, we will transition to policies dealing with the risk of cybersecurity. In the next blog, we will be diving into the adoption of cybersecurity insurance and the impact it has on traditional policies.
If you’d like to learn more about how Axio uses the four quadrants to determine the real impact of cyber events and help optimize insurance portfolios, don’t hesitate to reach out!




