Executive Summary
Federal support for critical infrastructure cybersecurity is more important than ever in these heightened times of the Ukraine-Russia conflict. There is growing concern Russia will engage in cyber-attacks targeting western critical infrastructure assets as retaliation for political interference. The United States private sector relies on the Department of Homeland Security’s Cybersecurity and Infrastructure Agency (CISA) for the latest best practices, intelligence, and collaboration tools. This article serves as an introduction to CISA’s important role in supporting the nation’s critical infrastructure sectors.
Financial Sanctions on Russia May Motivate Destructive Critical Infrastructure Attacks
Vladimir Putin’s invasion of Ukraine on February 24, 2022, has no end or resolution in sight. The West has imposed sanctions to limit Putin’s ability to access Russia’s $630B war chest. There is growing concern Russia will conduct retaliatory cyber-attacks on the US and other western countries for interfering with the invasion.
Many European and US-based businesses have already suspended operations in Russia and the list continues to grow every day.
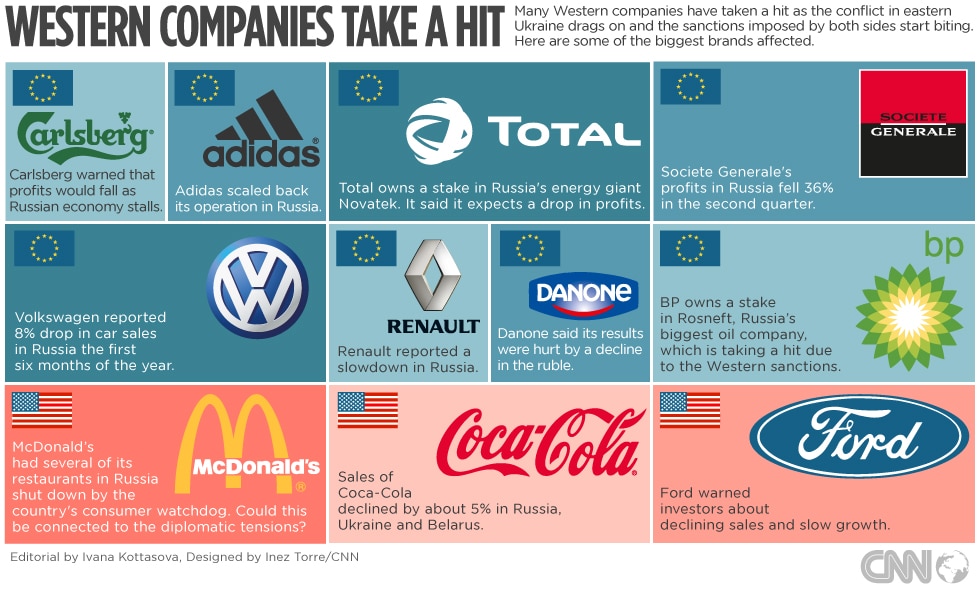 Due to Putin’s invasion of Ukraine, these western companies are either leaving the Russian Federation or pausing operations / Image credit: CNN
Due to Putin’s invasion of Ukraine, these western companies are either leaving the Russian Federation or pausing operations / Image credit: CNN
Russia has a history of engaging in destructive cyber-attacks targeting critical infrastructure such as Ukraine’s power grid in 2015 and 2016. And in 2017, malware called Not Petya was unleashed on Ukraine’s financial sector, spreading to millions of computers all over the world, disrupting supply chain operations of global companies such as FedEx and Maersk. Events of 2021 such as the SolarWinds breach as well as the ransomware attacks on Colonial Pipeline and JBS have been attributed to Russia as well.
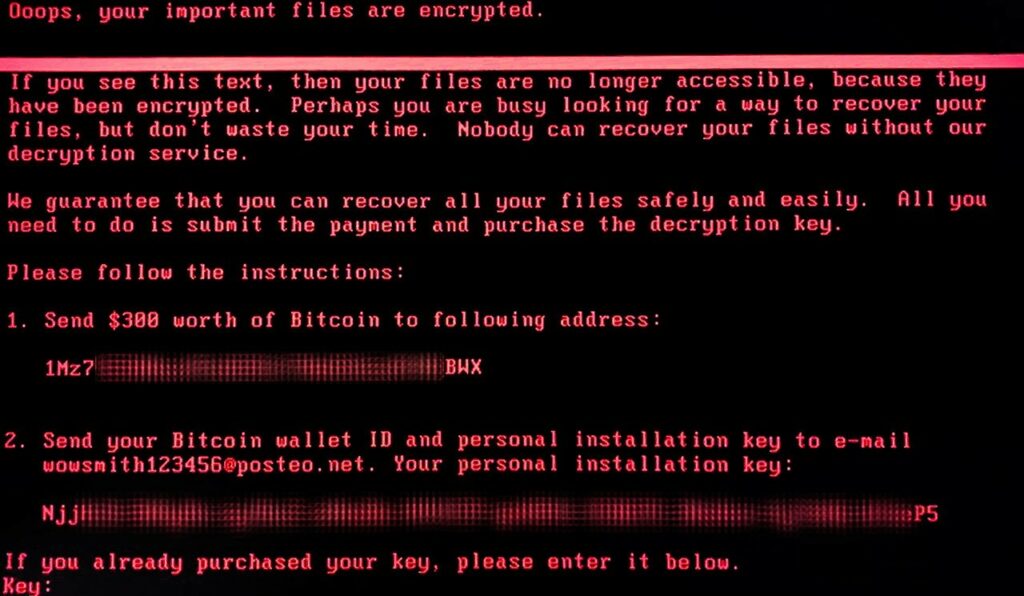
This is NotPetya’s ransom note displayed on a compromised system. The malware was designed to spread quickly, and that it had been targeting “complete energy companies, the power grid, bus stations, gas stations, the airport, and banks” according to Kaspersky.
US Critical Infrastructure is Fragile and Highly Susceptible to Cyber Interference from Nation States
Last year’s disruptions in the supply of gasoline, meat, and beer emphasized the fragility of US critical infrastructure. Ransomware attacks continue to be an appealing attack vector for nation-state cybercriminals. Business leaders continue to ask the question, “What if a Colonial-type event happened to us?” Critical concerns include:
- Will the business survive the attack?
- How much will the attack cost the business?
- What are the best initiatives to invest in today to be more secure by reducing exposure?
Immediate disruption of goods and services are devastating and have often resulted in an accelerated ransom payment. And to make matters more dire, the impacts of these types of cyber-attacks can lead to a humanitarian crisis and even death. Because victims pay ransom in Bitcoin and other forms of cryptocurrency, cybercriminals and their sponsors can bypass traditional monetary exchanges and ignore restrictions imposed by financial sanctions.
The notion a nation-state like Russia may resort to cyber-attacks was emphasized on March 21st, 2022, by a statement from President Biden on the nation’s cybersecurity. The statement urges United States private sector partners to harden their cyber defenses immediately and leverage best practices that were developed in partnership with the Department of Homeland Security’s Cybersecurity and Infrastructure Agency (CISA).
Protecting critical infrastructure deserves the highest level of attention on the federal level. Given rapid monetary inflation, a broken supply chain, and a healthcare sector tested to its limits by the COVID19 pandemic, the last thing the US needs is more logistical disruption. Enter CISA, the Cyber War General
A Closer Look at How CISA Came to Be
CISA is a federal agency within the Department of Homeland Security (DHS) and was established on November 16, 2018, when President Donald Trump signed into law the Cybersecurity and Infrastructure Security Agency Act of 2018.
According to CISA’s website their mission is to “build the national capacity to defend against cyber-attacks” and to work “with the federal government to provide cybersecurity tools, incident response services and assessment capabilities to safeguard the .gov networks that support the essential operations of partner departments and agencies.”
CISA connects stakeholders in public and private industry and government to each other and to resources, analyses, and tools to help them build their own cyber, communications, and physical security and resilience, in turn helping to ensure a secure and resilient infrastructure for the American people.
Before the Cybersecurity and Infrastructure Security Agency Act of 2018, federal cybersecurity responsibility was housed within the DHS but under National Protection and Programs Directorate (NPPD). The 2108 legislation elevated the importance of critical infrastructure cybersecurity to its very own federal agency with its own budget- a huge public relations win.
Even though CISA was formally established in 2018, there has long been a desire to develop a framework to prioritize the most critical infrastructure entities so stronger cybersecurity could be codified into law and subsequent federal support could be better managed.
In 2013, the Obama administration issued Executive Order 13636 which attempted to identify the “critical of critical.” The administration issued this order recognizing the risk of cyber-attacks “continues to grow and represents one of the most serious national security challenges we must confront.”
Section 9 of Executive Order 13636: A Company Specific Prioritization: Still Evolving in Focus
Section 9 of the Executive Order focuses on companies rather than systems and assets. There has been discussion about this language, and the reasoning behind it. Many believe that it’s easier to identify companies in possession of companies of critical systems rather than vice versa.
Unfortunately, Section 9 exempted the Information Technology sector, which proved to be a huge shortcoming in December 2020 during the SolarWinds hack. Many of SolarWinds clients were Federal entities and it is now obvious IT Sector is truly critical to national security as well public health, safety, and economic stability.
The Two Chief Centers of CISA
CISA is complex, with a multi-billion dollar budget and many initiatives impossible to cover in this brief article. However, in general terms, CISA is divided into two chief centers to achieve its mission. The first is the National Cybersecurity and Communications Integration Center (NCCIC). It provides 24 x 7 cyber situational awareness, analysis, incident response and cyber-defense capabilities to the federal government, other US jurisdictions, the private sector, and international partners. The other chief center is the National Risk Management Center (NRMC). It’s a planning, analysis and collaboration center working to identify and address the most significant risks to the nation’s critical infrastructure.
A Quick Note on NRMC and Shameless Plug of Axio360 to Identify and Address the Most Significant Cyber Risks to Critical Infrastructure
The NRMCC is more proactive and forward thinking and is critical for building a smarter and more resilient critical infrastructure. Here at Axio, we focus on these exact initiatives and will always believe and evangelize the importance of understanding and prioritizing your cyber risks so you can focus on the initiatives that matter most. It’s the motivation behind our desire to build the Axio360 platform, which takes an integrated approach to cyber risk. Think of it as a checklist (to assess your cybersecurity maturity), a calculator (for you to quantify your exposure), and a magnifying glass (to truly see what initiatives will matter most).
The truth is, you’re going to get breached no matter what you do. Instead of guessing what cybersecurity initiatives will provide the most protection, prioritize with confidence.
Curious how you can prioritize cyber risk? Schedule a demo to see Axio360 in action
The 16 Sectors of Critical Infrastructure According to CISA
CISA divides the nation’s critical infrastructure into 16 Sectors. The 16 sectors are: Chemical, Commercial Facilities, Communications, Critical Manufacturing, Dams, Defense Industrial Base, Emergency Services, Energy, Financial Services, Food and Agriculture, Government Facilities, Healthcare and Public Health, Information Technology, Nuclear Reactors, Materials and Waste, Transportation Systems, and Water and Wastewater.
These 16 sectors have “assets, systems, and networks whether physical or virtual so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.”
2018-2020, CISA’s Early Days
Having a federal agency with its own budget dedicated to critical infrastructure cybersecurity was a huge milestone for critical infrastructure owners and operators. However, the strategic direction and initiatives took time to get off the ground due to the sheer size and scope of CISA’s mission and lack of awareness and “brand recognition.”
In the first three years of its existence, the following are just a few of CISA’s many accomplishments:
- 2018: Presented a 5-year strategic framework to execute the government’s cybersecurity responsibilities.
- 2019: Released the inaugural set of National Critical Functions, which identifies functions so critical to the government and private sector, such as electricity distribution or internet service, that any disruption in them could cause debilitating effects on security, national economic security, national public health, or safety.
- 2020: Established CISA central website, telework guidance due to COVID-19, presidential election security, disinformation toolkit, and detailed guidance for Critical Infrastructure essential workers.
2021 and Beyond: Executive Orders Emphasize CISAs role in this Cyber War
The attack on Colonial Pipeline on May 6, 2021, made cybersecurity a mainstream news headline for many weeks and greatly accelerated the need for a federal response. Early in his term, President Biden made critical infrastructure cybersecurity a priority of the Department of Homeland Security (DHS) and reiterated the necessity for federal support.
On May 12, 2021, the President signed an Executive Order to improve the nation’s cybersecurity and protect federal government networks.
Most of the actions outlined in the Executive Order are to be implemented by CISA.
In the summer of 2021, Axio was proud of doing our small part in opening a necessary dialogue to protect electricity operations from increasing cyber threats. On July 7th-8th 2021, we hosted the Energy Cybersecurity Insurance Forum. This was part of a 100-day plan formalizing the Industrial Control Systems Cybersecurity Initiative. It was coordinated between the Department of Energy (DOE), the electricity industry and CISA. You can read the summary report here.
Senior administration officials said the 100-day plan has already led to over 150 electricity utilities representing almost 90 million residential customers deploying or agreeing to deploy control system cybersecurity technologies.
By the end of July, the Biden Administration signed the National Security Memorandum (NSM) on “Improving Cybersecurity for Critical Infrastructure Control Systems” which ordered CISA and the National Institute of Standards and Technology (NIST) to create benchmarks for organizations managing critical infrastructure.
New pilot plans like the 100-day initiative for electricity are in progress, with natural gas pipelines being next, followed by water systems, wastewater, and then the chemical sector. We envision CISA to play an important role in facilitating better information sharing and forward-thinking guidance and best practices.
With the first quarter of 2022 in the books, CISA’s Executive Assistant Director for Cybersecurity Eric Goldstein outlined four top priorities for the year and beyond. Summarized, they are:
- Enabling better threat intelligence by providing free resources and information sharing
- Building public-private partnerships since most of critical infrastructure is privately owned. Federal support needs a strong link between both public and private leaders.
- Developing a proactive cybersecurity strategy which includes scenario analysis. Cyber risk quantification (available in the Axio360 platform) helps you understand the worst-case scenario and align it to financial impact.
- Implementing security by design. Zero-trust has now moved from more than a marketing-buzzword to an entire security philosophy, that includes a capability maturity model.
Conclusion
Critical Infrastructure needs to be protected from cyber threats at all costs. With nation-states like Russia now posing as cyber-public enemy number one, a risk-based approach to cybersecurity is more poignant than ever. Cyber physical attacks are a major concern necessary to address now. According to Gartner, cyber attackers will have weaponized operational technology environments to harm or kill humans. This shifts the term cyber war to a marketing term to a real and present danger. We already witnessed a foreshadowing, with potential poisoning of the Oldsmar, Florida water supply. This is just one of many examples. CISA is rapidly working with various public and private entities to facilitate the necessary awareness, trust, and collaboration in this new era of cyber warfare. It’s a challenging endeavor given the sheer size of the many critical infrastructure sectors (such as water and wastewater) and the systems and assets they are responsible for. CISA has prudently taken a risk-based approach to cybersecurity, understanding that defend-all is not as important as defending what matters. With the many new cybersecurity initiatives spearheaded by the current administration, we see a bright future for protection of critical infrastructure. In subsequent posts, we’ll dive into the various sectors of critical infrastructure, highlighting various risk scenarios and areas of concern for owners-operators. After all, Axio is a quant company taking a risk-based approach to cybersecurity so you can be calm when the storm happens. When you know your security gaps and how much you have at stake, you can better plan the necessary cyber protection and ensure you survive.
In this post we discussed cyber risk quantification. If you are curious about our unique methodology, please don’t hesitate to book a demo.




