On Saturday, May 8th 2021, 45% of the United States east coast fuel supply was suddenly shut down. A dramatic visual of the states affected is presented below.
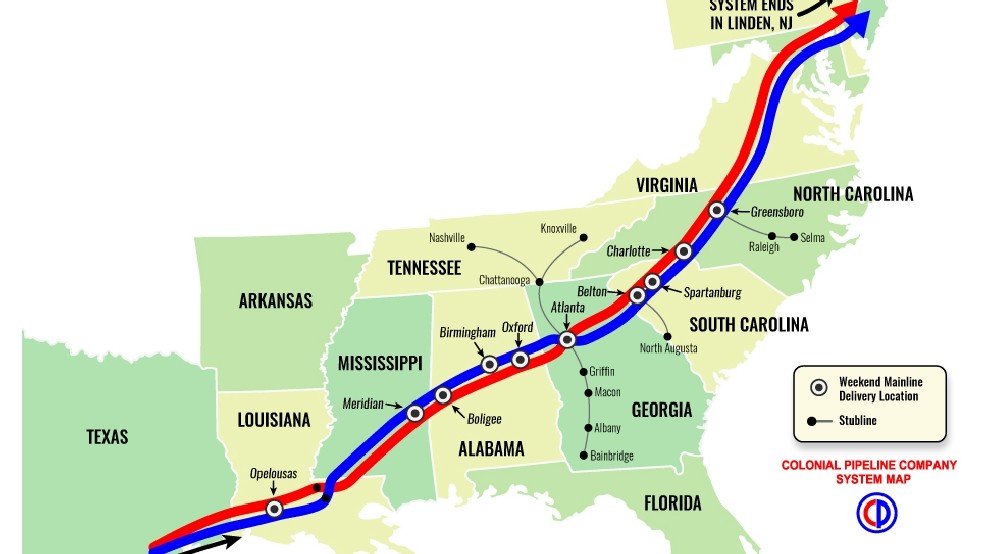
The pipeline, known as Colonial Pipeline, spans 5500 miles between Houston, Texas and Linden, New Jersey. The moment we heard the news, we feared the event was due to a cyber attack. At Axio, we spend every day leading workshops with critical infrastructure operators, helping them prepare and quantify the impact of such scenarios.
It didn’t take long for our suspicion to be confirmed. In a public statement, Colonial Pipeline Company said the cause of the shutdown was a ransomware attack on their IT network.
It’s not yet clear whether Colonial shutdown the pipeline out of an abundance of caution to stop the spread of the ransomware payload OR they can’t operate the pipeline due to dependencies on OT or IT systems. Axio has deep compassion for Colonial and all of their pipeline stakeholders and wish them the speediest possible recovery from this event.
This event builds on the insight from recent events in Texas, where natural gas pipeline issues resulted in statewide power blackouts, operational challenges to the power grid as far away as California, and more than $800m in commodity-price-related economic impact in Minnesota. The US economy is critically dependent on energy pipeline infrastructure. It is important for all energy-critical asset owners and the federal government to undertake risk analysis and economic quantification studies to understand the scale of impact from events like this and support investment in appropriate protections. The US economic impact from this event will likely be compounded by the recently reported shortage of qualified truck drivers for fuel transport.
Recommendations from the Cyberspace Solarium Commission include establishing a Public-Private Partnership on Modeling Cyber Risk and a Bureau of Cyber Statistics charged with collecting and providing statistical data on cybersecurity and the cyber ecosystem to inform policymaking and government programs. This event combined with the recent events in Texas highlight our critical dependence on energy pipeline infrastructure and the importance of quick action on these and other recommendations from the Commission.
The pipeline industry, in collaboration with API, INGAA, and AGA, have been attempting to get ahead of pipeline cybersecurity issues with the update to the API 1164 standard. Axio intends to support our users by making the standard available in our Axio360 platform as soon as possible after the API balloting process is complete. This standard is a critical step forward in supporting pipeline cyber protections and limiting US economic impact from disruptions like this.
The Colonial event points out the critical importance of preparing for ransomware events. The following are three steps companies should be taking to stop malicious actors from gaining access to critical systems:
- Increase Protections to Privileged Credentials. Arguably, the most important thing companies can do to fight ransomware is to create new protections for privileged credentials. Essentially, too many employees and third-parties have passwords and access to company infrastructure. To remedy this, companies should be investing in multi-factor authentication solutions for domain administrator accounts, scrutinizing domain admin privileges, and eliminating domain admin service accounts.
- Modernize Endpoint Protections. Most companies today have many “endpoints” for the network, which include laptops, desktops, cell phones, and tablets. These endpoints create security vulnerabilities for the entire corporate network because the people using them are susceptible to phishing scams and hacks. Despite having so many endpoints, companies are often too trusting of established malware lists and don’t have software to look for new threats proactively. Companies can remedy this with advanced anti- malware software, the usage of firewalls and intrusion detection systems, and sandboxing.
- Improve Vulnerability Management. While it might sound like an obvious thing to do, companies today need to keep all of their hardware and software up to date with software patches. The sad fact is administrators often let patches sit for too long before being implemented, creating a window where a cybercriminal can gain easy access to the network because the vulnerability is widely known. Additionally, admins should be actively working to reconfigure permissions, so fewer people and devices have access to the network.
Axio’s free ransomware preparedness assessment provides companies of all sizes with critical guidance to prevent, contain, and restore ransomware events. Our work with companies to financially model cyber risk events, like ransomware, is used by many critical infrastructure owner/operators to prioritize their investments to protect against events of this type. Axio’s ransomware preparedness assessment is available in our free online tool. We also recently broadcast a webinar on ransomware trends and prevention, including attack patterns for big-game-hunting ransomware.
Axio is an expert in the financial impact modeling of cyber risk events. Using the Axio360 software, our clients are able to quickly, effectively, and transparently model potential cyber risk events, which is critical to informing investment priorities for responding to cyber risk. Axio’s method is scenario-based, which is a highly effective way to understand the complexities of inter-system dependencies, such as those that often exist between IT networks and OT networks. Such interdependencies can often be overlooked in asset-centric risk analysis approaches.
Book a confidential consultation with Axio’s ransomware modeling team.




