On July 27, 2020, the North American Electric Reliability Council (NERC) released an updated mapping of the Critical Infrastructure Protection (CIP) Reliability Standards to the National Institute of Standards Framework for Improving Critical Infrastructure Cybersecurity, commonly known as the NIST Cybersecurity Framework (NIST CSF). For the uninitiated, the NERC-CIP establishes standards and imposes regulations pertaining to the security requirements for bulk power systems. The newly released mapping will be a useful tool for those organizations within the electric power and utility industry that must adhere to NERC CIP compliance.
NERC CIP Magnified by NIST CSF
Previous mappings of NIST CSF to NERC CIP had become obsolete with an updated version of the CSF released in April of 2018. This coupled with new standards as part of NERC CIP over the years rendered previous mappings to be no longer useful.
As background, the NERC CIP Reliability Standards derive from the Federal Energy Regulatory Commission (FERC) Order No. 706, which was issued in January of 2008. The CIP Standards have been updated over the past twelve years to address the constantly evolving types of cybersecurity threats to the bulk electric system (BES).
At present, the CIP Reliability Standards consist of 13 standards that specify a set of requirements that registered entities must follow to ensure the cyber and physical security of the bulk power system. Currently, there are 10 active cybersecurity standards and 2 (CIP-012-1 and CIP-013-1) that will be effective in the near future.
The 13 CIP reliability standards for cyber and physical security of bulk power are as follows:
- CIP-002-5.1a: Bulk Electric System Cyber System Categorization: Requires entities to identify and categorize BES cyber elements and their associated cyber assets for the application of cybersecurity requirements using a tiered approach commensurate with the adverse impact of their loss, compromise, or misuse. In addition it requires that any communication and data flows between the BES Cyber Systems and other systems like physical security and business systems be included in the documentation.
- CIP-003-7: Security Management Controls: Requires entities to specify consistent and sustainable security management controls to protect BES Cyber Systems against compromise that could lead to misoperation or instability in the BES. For example, policies must comprise obligations for user training and security awareness. The new mappings underscore the importance of NERC CIP training, in the next reliability standard too.
- CIP-004-6: Personnel and Training: Requires the minimizing of risk against compromise that could lead to misoperation or instability in the BES from individuals accessing BES Cyber Systems by requiring an appropriate level of personnel risk assessment, training, and security awareness. For instance, it requires entities to define a formal process in written or workflow format for managing logical system access including granting of access and periodic review of permissions.
- CIP-005-5: Electronic Security Perimeter(s): Requires entities to manage electronic access to BES Cyber Systems by specifying a controlled Electronic Security Perimeter in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the BES. To further establish electronic security perimeters, it requires implementation of formal procedures and processes for the proper separation of the environments for test and production networks.
- CIP-006-6: Physical Security of Bulk Electric System Cyber Systems: Requires entities to manage physical access to BES Cyber Systems by specifying a physical security plan in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the BES.
- CIP-007-6: System Security Management: Requires entities to manage system security by specifying select technical, operational, and procedural requirements in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the BES.
- CIP-008-5: Incident Reporting and Response Planning: Requires entities to mitigate the risk to the reliable operation of the BES as the result of a cybersecurity incident by specifying incident response requirements.
- CIP-009-6: Recovery Plans for Bulk Electric System Cyber Systems: Requires entities to recover reliability functions performed by BES Cyber Systems by specifying recovery plan requirements in support of the continued stability, operability, and reliability of the BES.
- CIP-010-2: Configuration Change Management and Vulnerability Assessments: Requires entities to prevent and detect unauthorized changes to BES Cyber Systems by specifying configuration change management and vulnerability assessment requirements in support of protecting BES Cyber Systems from compromise that could lead to misoperation or instability in the BES. Among other specifications, it also requires entities to utilize monitoring tools for ensuring integrity of baseline configurations when stored outside of a protected zone.
- CIP-011-2: Information Protection: Requires entities to prevent unauthorized access to BES Cyber System Information by specifying information protection requirements in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the BES.
- CIP-012-1: Communications between Control Centers: Requires entities to protect the confidentiality and integrity of real-time assessment and real-time monitoring data transmitted between Control Centers.
- CIP-013-1: Supply Chain Risk Management: Requires entities to mitigate cybersecurity risks by implementing security controls for supply chain risk management of BES Cyber Systems.
The Importance of Mapping NIST CSF to NERC CIP
Numerous organizations in the North American critical infrastructure energy sector must be compliant with the NERC CIP Standards. Many of these organizations have implemented the higher-level CSF separately from the more specific NERC CIP compliance requirements. However, when implementing security standards, they ideally shouldn’t stop their compliance activities with NERC CIP but leverage NIST CSF. By mapping the two together, an organization can be more secure and effective in assessing and implementing strong security controls.
To understand the importance of using NIST CSF as a lens for NERC CIP CIP, it’s important to note that the controls outlined in the CSF exceed those of the CIP requirements that are more compliance based, although the former are not as prescriptive.
The recently released mapping from NIST CSF to NERC CIP will be of great benefit to the organizations in the electricity industry. The tool lists the CSF Categories and Subcategories and maps them to the specific CIP requirements. It also includes the mapping logic, as well as specific guidance for the use of the combined framework and standards of NERC CIP vs. NIST CSF. The mapping also provides a reverse approach that maps the CIP requirements to the CSF Subcategories. Examples of these two approaches to the mapping can be viewed in the following diagrams.

NIST CSF with mapping to NERC CIP
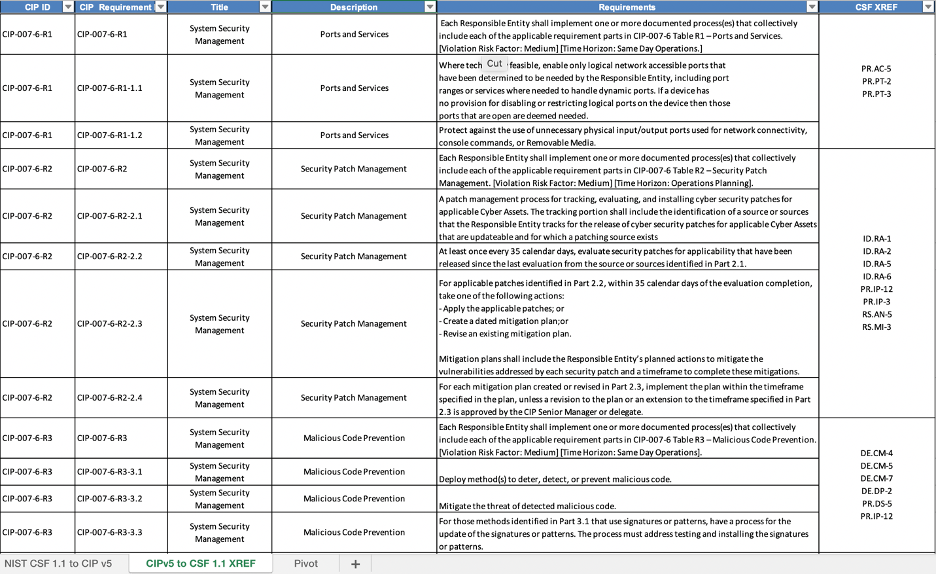
NERC CIP with mapping to NIST CSF
Recent FERC White Paper envisions incentives for cybersecurity investments
On June 18, 2020, FERC issued a Cybersecurity Incentives Policy White Paper. The white paper, which can be found on the FERC website, discusses a potential new framework for providing transmission incentives to utilities for cybersecurity investments. This new framework would review and provide benefits to those organizations that exceed the requirements of the NERC CIP Standards. FERC stated that “transmission incentives to counter the evolving and increasing threats to the cybersecurity of the electric grid may be warranted.” NERC CIP categorizes assets as high, medium, and low impact systems. While all the standards apply to the high and medium risk assets, only a few apply to the low impact assets.
The white paper outlines two paths for an organization to identify and implement cybersecurity investments. The first would call for the implementation of medium or high security controls for facilities identified as low or medium impact systems. The second approach would award incentives based on an organization implementing portions of the NIST CSF to its assets.
With the newly released mapping, it can be a bit challenging to determine which of the two standards would be applicable or more beneficial in terms of cybersecurity incentives in any given situation. In such cases, it would help to remember that although the CIP standards would still be the basis for granting cybersecurity incentives, organizations would have the flexibility of non-prescriptive options from the NIST CSF that would exceed the CIP Standards.
NIST CSF in the Axio360 platform with mapping to NERC CIP
Axio has already implemented the mapping of the NIST CSF to the NERC CIP informative language in the Axio360 platform. This allows the utility end-user to be more effective at navigating the NIST CSF Categories and Subcategories to the CIP requirements and informative language. This will also facilitate the tracking of multiple other models and frameworks along with the NIST CSF and NERC CIP standards.

NIST CSF Assessment Interface in Axio360 with mapping to NERC CIP
If you’d like to experience the complete functionality of NIST CSF with mapping to NERC CIP and discuss your particular use case for the framework, our experts are standing by. To take the first step towards increased cyber security, book a customized demo today!
About the author: Eric Cardwell is a Director of Cyber Risk Engineering at Axio




