CRQ: A Balanced Approach to Critical Infrastructure Protection
Welcome back to the final part of our cyber risk highlights series on critical infrastructure. If you are tuning in for the first time, here’s a recap of the previous four parts of the series:
Part 1: Why cyber risk needs to be understood and prioritized for critical infrastructure
Part 2: Why cyber-attacks target critical infrastructure control systems, not data.
Part 3: How ransomware attacks create collateral damage, emphasizing the delicate relationship between IT and OT.
Part 4: Why preparing for cyber-attacks highly depends on mastering the basics for ransomware readiness.
This week, we conclude our series by demonstrating how new approaches to cyber risk quantification (CRQ) can improve critical infrastructure resilience, including the increasingly publicized cyber insurance coverage conundrum.
Ensure Survival: Estimate Probability Faster to Focus on Impact
The ultimate test of an organization’s cyber resilience is whether it has the financial wherewithal to survive a cyber event. This is when cyber risk quantification (CRQ) creates the necessary balance of cyber protection. Quantification clarifies what to focus on and reduces uncertainty by expressing cybersecurity risks in financial currency. Quantification has existed for a while, but many methods adopted in the mainstream have been singularly focused on probability. This approach is not realistic for owners and operators of critical infrastructure.
Quantification methods strictly based on probability are time-consuming because they are granular and require a great deal of analysis. Having a precise probability of an event is appealing but can be plagued with complexity and bottlenecks due to granularity. One can spend months upon months estimating various probabilities and multiplying them with each other. What does one gain from this exercise if the probability is non-zero? Because there’s a reasonable chance of suffering the impact, the organization gets more value from knowing the financial consequences so they can endure the impact.
Balancing Time and Value: Evolving Cyber Risk Communication and Decision-making
The image below is an example of what’s possible with cyber risk quantification when focusing on impact first. In this anonymized output from an Axio client, a CISO was making a budget argument for deploying up to 5 new (or improved) controls in the organizations.
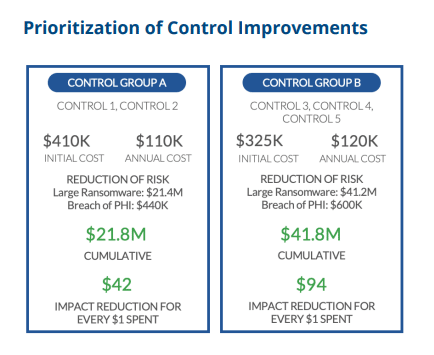
You can see the controls split into group A and group B. The CISO thought he could only get funding for the two controls in group A. However, the organization needed the controls in group B as well. By focusing on impact, it’s easy to explain the greater return on investment by implementing both control groups.
Don’t Forget about Insurance as a Control
When developing a cybersecurity program, a measured balance of technology and insurance is pivotal to success. There’s increased demand for cyber insurance after the many high-profile ransomware attacks of the past few years, and many organizations have realized the need to supplement their technology controls with risk transfer mechanisms like cyber insurance. Pre-COVID, a cyber insurance policy was typically attainable via a simple questionnaire application. At present, however, the exigent ransomware climate has complicated the process for insurers, as they cannot afford to be as lenient as yesteryear.
Underwriting a cyber insurance policy exposes insurers to greater risk than it has in the past, and owners and operators of critical infrastructure will have to meet more stringent cybersecurity requirements to qualify. We have already seen this situation unfold in the water and wastewater sector, and the topic was emphasized at the National Association of Water Companies (NAWC) conference. These requirements include secure access management programs for protecting administrative credentials with privileged accounts, as well as endpoint detection and response tools.
For insurers, a cybersecurity assessment only provides a snapshot in time and is only one part of the solution they need to certify insurability. Cyber risk quantification completes the picture, giving insight into improvements and initiatives that should be prioritized within the program. This kind of financial visibility will provide more clarity for insurance underwriters.
Closing Thoughts
In the previous sections of our blog series, we’ve highlighted the sophistication of cyber criminals with various toolkits, how easily they can launch ransomware attacks to leverage IT and OT interdependencies, their ability to cause physical damage without even accessing control systems directly, and the general lack of preparedness many organizations currently experience. Time is not on your side.
Assessing your cybersecurity gaps is a critical first step. But the output can be overwhelming, particularly if your cyber posture is low to begin with. What should we do first? This is a question often asked by cybersecurity teams.
So, for those seeking to improve their cyber-protection situation and reduce their risk, what can they do in the shortest amount of time to produce the greatest value? And when we speak of value we talk about survival.
The answer lies in a more efficient and scalable way to quantify cyber risk. At the end of the day, to be resilient, you need to:
- Communicate cost and benefit in financial terms
- Avoid focusing only on probabilities
- Quickly compare potential cybersecurity investments.
Not all organizations can afford to build up a larger cybersecurity team or buy every solution under the sun to lower their cyber risk. Legacy, long-term approaches originally designed to help with prioritization, may be counterintuitive now for smaller owners and operators of critical infrastructure. Laborious quantification methods may create unnecessary processes in larger organizations and take up to 6 months to demonstrate results.
With many critical infrastructure operators classified as small and medium-sized businesses, and larger organizations dissatisfied with the “old way” of doing cyber risk quantification, we believe we’ve found a better way to protect systemically important critical infrastructure.
When you can communicate your critical cyber scenarios faster, you can achieve necessary resilience. Value is gained as soon as you start to reduce uncertainty—in this case, about the financial impact of key risks. The most value is gained from ‘zero’ knowledge to initial impact estimations. You immediately start to see where the largest type of impacts arise and can focus your additional efforts on either better understanding those impacts or making the investment to reduce them.
CRQ supports many use cases and delivers actionable results. If you’ve tried CRQ and found it cumbersome, daunting, or an expensive waste of resources, chances are you’ve been ensnared by the constraints of an asset-based only approach. The new CRQ market provides a practical solution to outdated and inefficient legacy solutions. Sign up for a free demo to learn how you can successfully leverage CRQ using risk scenarios and business impact.