If the ubiquity of the Rotten Tomatoes platform teaches us anything, it’s that we tend to rely on aggregates, or a mass common denominator, because an average response brings us comfort through generalizations. But if this one-size-fits-all approach works in helping us make seemingly informed decisions, the downside is that the perceived efficiencies are traded in for nuance and customization.
Moreover, the problem in this approach in regard to cybersecurity is that there has to be a custom consideration. For example, some companies risk environmental damage if certain systems fail, so they have to pay special attention to those networks. Others have massive warehouses of healthcare data that if compromised, leads to the private information of unaware individuals is available for third party access. For a CISO to recommend a security protocol based on the general consensus of their colleagues means a lack of deep consideration and foresight.
An Optimal Cyber Budget Needs a Good Story to Support It
A good CISO is to a certain extent a good storyteller–they need to create a narrative that feels developed, structured, and compelling. They need to paint a picture that conveys authenticity and urgency, which means describing a worst-case scenario which makes clear the possible catastrophic impacts of a bad cyber day. Asking hard questions is uncomfortable, but it’s important to remind a CEO about the potential of being called before congress to defend losing everyone’s private information or having to make an announcement about a toxic spill.
But while worst-case scenarios must be considered when positioning potential outcomes, there are instances in which a corporation can even relax certain programs–the prospect of removing a safeguard is rather frightening but it’s worth asking yourself whether two-factor authentication for every single user is an effective utility in preventing attacks or is it required only for more privileged accounts.
The Cyber Story is in the Metrics
This is not to say that a cyber security strategy presentation is a creative writing exercise–the most effective story drives from metrics. These metrics need to not only capture the conditions inside the company that create risk but the potential impacts in dollar terms. With an understanding of what is driving risk and what is contributing to the financial impact, the CISO more easily identify the necessary organizational changes and as importantly, justify them. Combining metrics, expected losses, existing budgets for the cyber program, and expense projections for proposed improvements creates a more informed case that couples cold calculations with the necessary context from impactful storytelling.
But ultimately, the only way you can get concurrence that’s meaningful and durable is by walking all participating parties through the process in a transparent way. When the CISO is asked to tell us what’s possible, it’s their imperative to get in touch with the legal department and ask them what happens if we have legal issues based on a breach, or go to the contract department and ask them what happens if we aren’t able to fulfill our contracts. This way everyone feels invested in a cyber security program and everyone understands the value. And when there’s a cumulative support and a deep-rooted interest in the program’s success, you not only have the data, but you have the ideal.
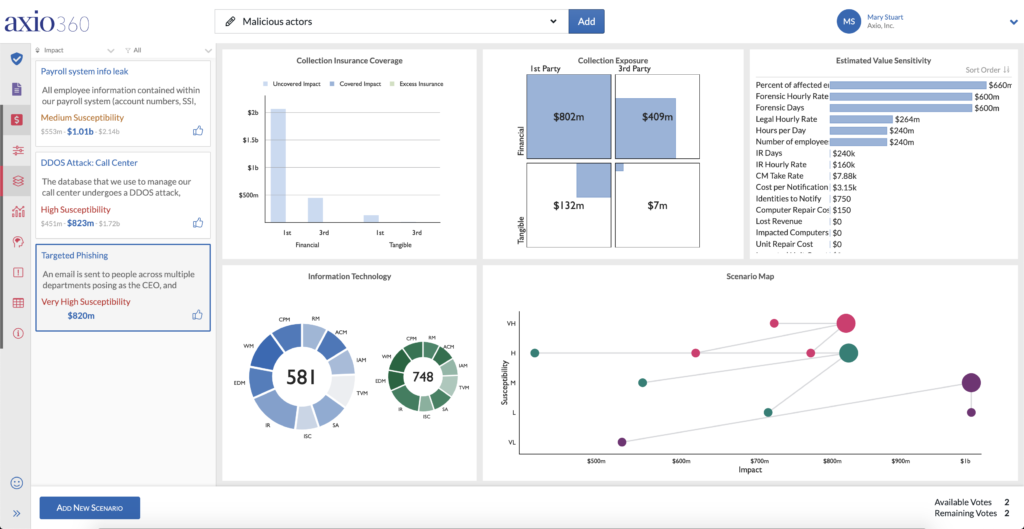
Impactful storytelling means demonstrating how implementing a group of security controls can directly lead to risk reduction, in dollar amounts. The Axio360 Control Initiatives dashboard provides this capability. To see the Axio360 Control Initiatives feature in action, you can book a demo today.